Landfall Spyware Targeted Samsung Phone Flaw, Attackers Still Unknown
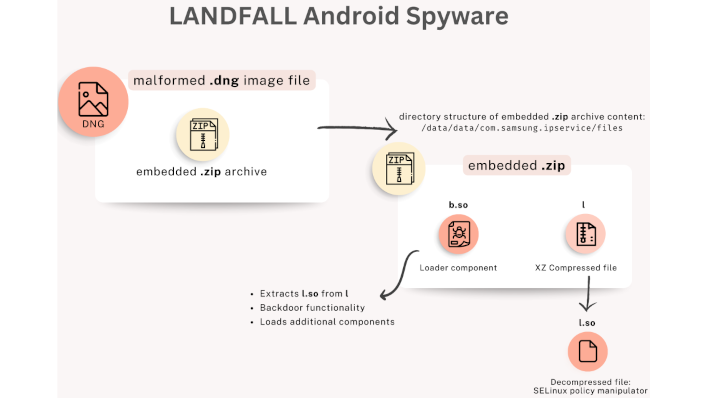
Thankfully, the CVE-2025-21042 vulnerability that provided the attack vector for this spyware has been patched by Samsung since April 2025. But this was only after the attack was already in use since at least mid-2024, and Unit 42's research indicated that the attack was used for comprehensive surveillance of compromised devices in the Middle East. Surveillance functions included "microphone recording, location tracking, and collection of photos, contacts, and call logs". The malformed image files used to carry the attack were sent to victims via WhatsApp and subsequently burrowed deep into the system, remaining active and undetected for months until Samsung's patch for the underlying vulnerability was released.
So, fortunately for current Samsung and Android users, there's no immediate cause for concern. As long as you've patched your Android phone since April 2025, you're most likely safe from this specific attack and the vulnerability it exploited. However, it does show a concerning trend in zero-click attacks on Android devices that don't even require users to download an application or misclick on a web page, which makes careful curation of browsing destinations and contacts even more important for those trying to protect their privacy. Many new pieces of malware no longer require user ignorance to exploit—now, just being the recipient of an innocuous image file on an unpatched device could be a precursor to a malware infection.
The full Unit 42 report is available on Palo Alto Networks' blog, and goes into far more details on the specifics of this attack and how it and its contemporaries do their work. Knowledge of attacks like these emphasize the importance of security updates and up-to-date knowledge of cybersecurity, but especially for government or private sector employees dealing with highly-sensitive information.


