When Microsoft added
Windows Subsystem for Linux it was exciting for developers, but it also raised a question. "If Windows can run Linux, when will it run Android?" A logical inquiry of course, because Android is a Linux-based operating system. Unfortunately, now that Android Subsystem has been added, a bad egg has already caused problems for some people.
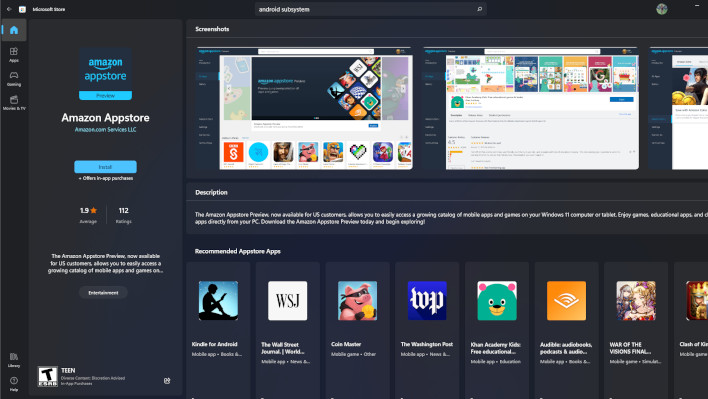
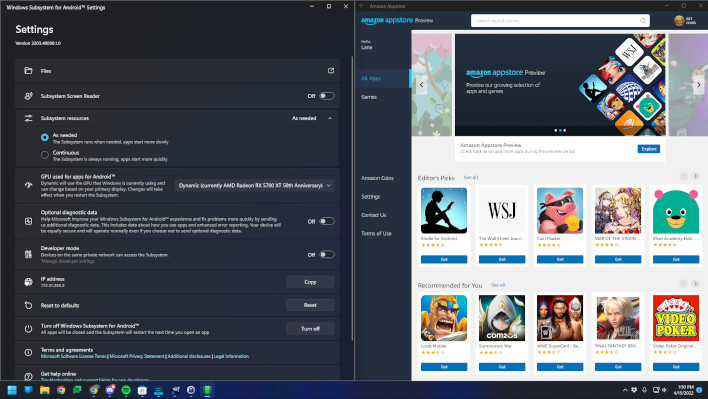
Much to the disappointment of many
Android fans, the Android Subsystem for Windows only included the Amazon App Store. That was a bit of a headache and annoyance for anyone who wished to use it and use Google Play apps. However, Android is not particularly difficult to do some side loading. So, some third parties took a bit of time to work on making it so that Google Play Store side loading could be implemented quickly and easily. Unfortunately, one particularly popular tool known as PowerShell Windows Toolbox looks to have managed to hide a nasty Trojan in it.
The PowerShell Windows Toolbox tool touts the ability to "debloat Windows 10 or 11", make modifications to make the OS more efficient, forcibly turn Windows Update off, activate
Microsoft Office, install Google Play for Android Subsystem, and a few other features.
Unfortunately, hidden within the project's code are a couple of pieces of malware. These pieces of code are obfuscated. When de-obfuscated, it was discovered that the tool actually will use its PowerShell access to install an iffy browser extension. It additionally will copy browser profiles, and then start to serve up several scam pop-ups and prompts. It also creates a folder on the root of the Windows drive, which for most people is C:\ called "systemfile". The tool even places a scheduled task that looks to try to download even more malware.
An interesting facet of this particular example of hidden malware is that the fact that the project's open-source nature is what allowed people to discover its nefarious deeds. This, in our opinion, is an example of open source showing one of its greatest benefits—the idea of communal code review.
Once caught Github pulled the project and it is currently serving up an Error 404 page for the project's address. You can still view some cached content of the people reporting the malicious code in the project's
Github issues though. As with any software it is always best to vet your sources from with your software came, and in the age of open source, it might be worthwhile to check the issues log as well, as sometimes, you might see someone reporting malicious code!
Perhaps to prevent this in the future, Microsoft's new
Android-focused-team could implement Google Play Store on their Android Subsystem themselves, we're not holding our breath though.