Researcher Claims TikTok Could Be Secretly Tracking Your Keystrokes
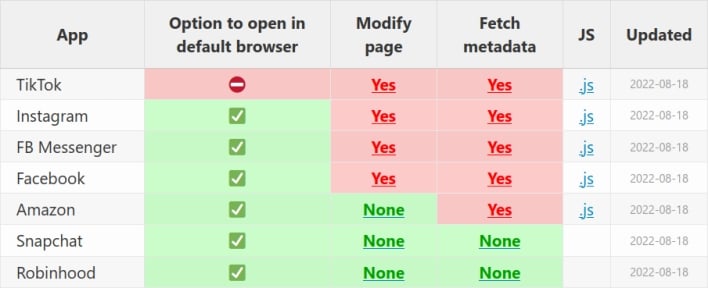
Many mobile apps let users click on links and visit the linked webpages within the app, rather than opening the device’s default browser app. Apple offers a restricted Safari viewport that developers can include in their iOS apps for this purpose. However, developers can also create their own in-app browsers, and it turns out that some developers build their own in-app browsers to inject JavaScript into webpages.
Felix Krause first discovered this behavior in Meta mobile apps, but he didn’t stop his searching there. After developing a rudimentary tool to detect JavaScript injection for his research on Meta apps, the researcher decided to develop this tool into one that can be used by the public. He then went to work testing more in-app browsers with this tool. What this further research shows is that TikTok’s in-app browser injects even more invasive code than the in-app browsers in Meta apps.
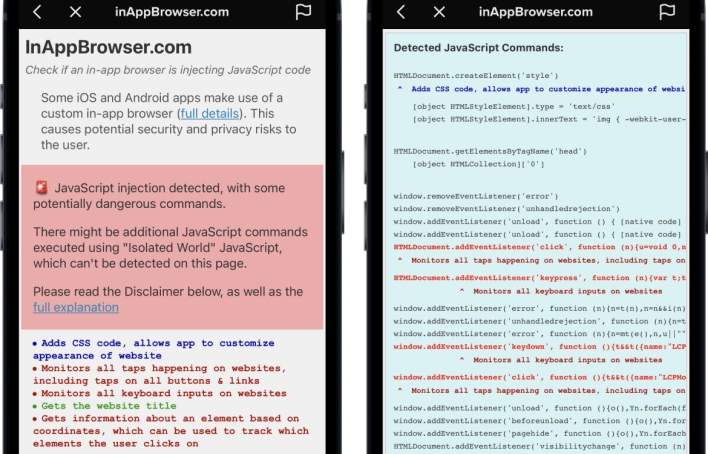
Krause’s JavaScript injection tool revealed that TikTok’s in-app browser injects code that listens for every key input entered into webpages viewed within the app. This means that TikTok could potentially record all text, including passwords, credit card details, and any other sensitive information entered into websites accessed by way of its in-app browser. The TikTok mobile app also injects code that can detect every tap on webpage elements, such as buttons, links, and images, and read the name of each element as users interact with it. In addition to injecting this JavaScript, unlike many other in-app browsers, TikTok’s in-app browser doesn’t include an option allowing users to open webpages in their devices’ default browsers. Thus, if users want to avoid TikTok’s in-app browser, they have to manually copy links shown in the app and paste them into the browser app of their choice.
In a statement reported by Forbes, Maureen Shanahan, a spokesperson for TikTok, acknowledged that its in-app browser injects code, but said that it has a legitimate use. “Like other platforms, we use an in-app browser to provide an optimal user experience, but the Javascript code in question is used only for debugging, troubleshooting and performance monitoring of that experience — like checking how quickly a page loads or whether it crashes.”