Microsoft Warns About LemonDuck Monero Crypto Malware Ravaging Windows, Linux PCs
Such is the same with LemonDuck, which the Microsoft 365 Defender Threat Intelligence Team is warning about this week. Once LemonDuck malware finds its way onto a target machine, it is swept up into a botnet that mines for cryptocurrencies. What makes LemonDuck so dangerous, however, is that it doesn't just target one platform. Instead, it is viable on both Windows- and Linux-based computers.
According to Microsoft, LemonDuck can propagate via phishing emails, brute force, USB thumb drives, and security exploits. Concerning the latter attack vector, LemonDuck is adept at exploiting the following security vulnerabilities on unpatched systems:
- VE-2017-0144 (EternalBlue)
- CVE-2017-8464 (LNK RCE)
- CVE-2019-0708 (BlueKeep)
- CVE-2020-0796 (SMBGhost)
- CVE-2021-26855 (ProxyLogon)
- CVE-2021-26857 (ProxyLogon)
- CVE-2021-26858 (ProxyLogon)
- CVE-2021-27065 (ProxyLogon)
Microsoft states that LemonDuck spreads its wings to infect additional machines via "edge-initiated" compromises, bot implants "moving laterally" throughout an organization, or with bot-initiated email campaigns.
"Once inside a system with an Outlook mailbox, as part of its normal exploitation behavior, LemonDuck attempts to run a script that utilizes the credentials present on the device," writes the Microsoft 365 Defender Threat Intelligence Team. "The script instructs the mailbox to send copies of a phishing message with preset messages and attachments to all contacts."
"After the emails are sent, the inbox is cleaned to remove traces of these emails," the team continues. "This method of self-spreading is attempted on any affected device that has a mailbox, regardless of whether it is an Exchange server."
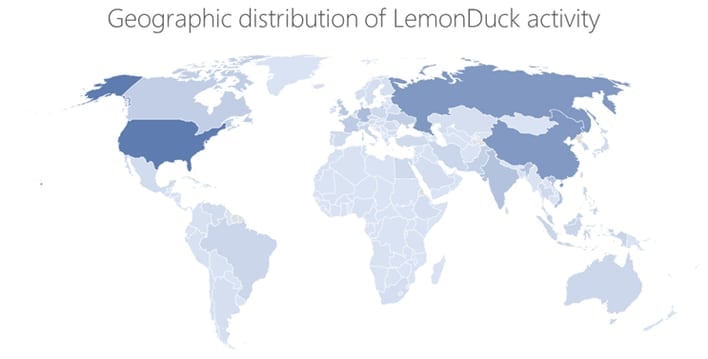
The primary motive behind LemonDuck is to mine for Monero, which is a frequent choice for these malware campaigns. While LemonDuck initially targeted China heavily, it has expanded to infect systems in the United States, Russia, China, Germany, the United Kingdom, India, Korea, Canada, France, and Vietnam.
Not surprisingly, Microsoft is pointing to its own 365 Defender and Defender for Endpoint security solutions to detect and block the spread of LemonDuck on both Windows and Linux systems.


