McDonald's, Coca-Cola Among Impersonated Brands In Massive Phishing Campaign
The phishing campaign spreads over WhatsApp beginning with messages sent to unsuspecting users. These messages contain links that redirect users to surveys bearing branding belonging to various trusted brands. According to Cyjax, the campaign currently imitates over 400 brands. The links shared over WhatsApp send users to a domain controlled by Fangxiao while specifying which brand to impersonate. The initial domain visited by each user then redirects the user to another domain where the branded survey resides.
Fangxiao frequently rotates both the landing and survey domains, switching them out for newly registered domains in an attempt to prevent cybersecurity personnel from enumerating and blocking the phishing campaign’s internet infrastructure. While monitoring this campaign, Cyjax researchers observed over 300 unique, newly registered domains in a single day.
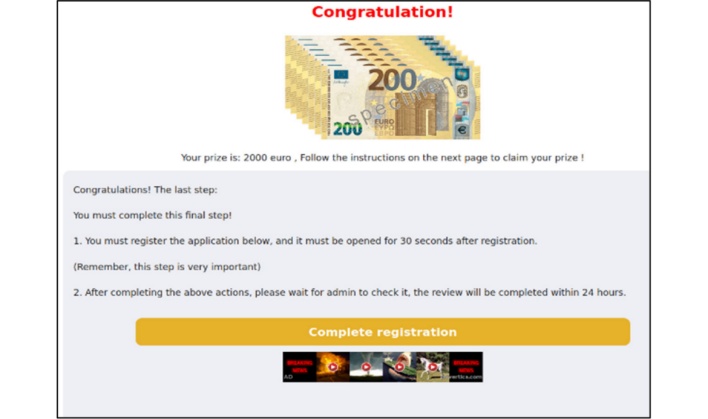
After tapping up to three boxes, the user “wins” a prize usually consisting of a high value gift card. In order to claim the prize, the user is asked to share the survey with friends on WhatsApp. When the user taps the share button, the website generates unique URLs to be shared with contacts on WhatsApp, further spreading the phishing campaign. After filling up a progress bar by hitting the share button thirteen times, the user is sent to a final page controlled by Fangxiao.
This webpage includes a final set of instructions for claiming the prize, but also displays advertisements. These ads, when clicked, quickly redirect the user through multiple domains before arriving at a final destination that varies based on the device’s operating system and IP address. Using different devices and IP locations, the researchers observed various destinations, including a SMS micropayment scam, an Amazon affiliate link, and an automatic download of a malicious Android APK file.
Users who ignore these ads on the survey site and proceed with the final step by clicking on the “Complete registration button” are sometimes sent down a similar redirection rabbit hole. However, clicking on this button on an Android device will either download a malicious APK or redirect users to a fake cleaner app on the Google Play Store that functions as adware.

