Beware, Robin Banks Phishing Campaign Is Back To Steal Your Cash In Its Next Big Heist
Since Robin Banks functions as a phishing-as-a-service platform, the threat actors behind the platform don’t simply develop and distribute phishing software. They instead operate the infrastructure necessary to carry out sophisticated phishing attacks, then provide phishing toolkits that make use of this infrastructure to other cybercriminals who pay monthly fees. The paying customers rely on the Robin Banks server infrastructure, expecting it to be fully operable 24/7.
Like many online businesses, the threat actors responsible for Robin Banks were previously using Cloudflare to protect their servers from DDoS (distributed-denial-of-service) attacks, but, after Cloudflare blacklisted Robin Banks, the threat actors switched to DDOS-GUARD. DDOS-GUARD is a Russian-based DDoS protection and web hosting service known to unapologetically provide its services to cybercriminal and terrorist groups. It took only three days from the time Cloudflare blocked the Robin Banks domain names for the platform’s developers to migrate the infrastructure to DDOS-GUARD and bring it back online.
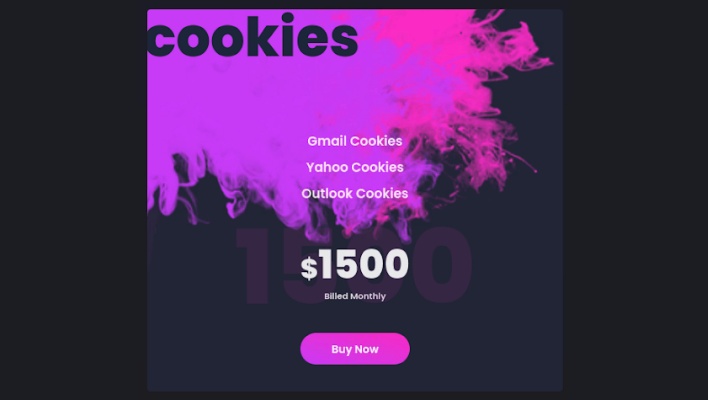
Despite using an open-source tool that other cybercriminals could use themselves, Robin Banks charges customers a premium of $1500 a month on top of the regular $200 monthly fee for use of this cookie-stealing feature. According to IronNet, Robin Banks utilizes many other open-source tools as well, demonstrating the low barrier to entry for operating a PhaaS platform. There are still plenty of threat actors that develop their own proprietary hacking tools and malware in addition to maintaining the infrastructure necessary to conduct cyberattacks. Nonetheless, the availability of many malicious open-source tools is leveling the playing field, enabling less experienced cybercriminals to enter the PhaaS space.

