The Global Smartphone Privacy Problem: Spy Tools Discovered Monitoring Billions
There's actually a few individual flags here, but they all have the same end result. The first report is simpler; an investigation by cybersecurity researchers Mysk revealed that iOS devices can use the window provided by push notifications to capture data from your phone and send it to remote servers, even if the app itself isn't actually running on your phone. That's right: even apps you aren't using can be tracking you.
So okay, just avoid downloading any shady apps and you won't have to worry about this, right? Wrong. Mysk uncovered an incredible number of apps that phone home with push notifications, including familiar names like Facebook, X (Twitter), LinkedIn, Instagram, Threads, Tiktok, and many, many more. Data captured includes such specifics as available memory, battery status, and even display brightness.
You might think, "well whatever, I don't care if they have that kind of data," but exactly those kinds of details can be used to create a digital "fingerprint" of your device that can then be used to track you across multiple domains. Fingerprinting is strictly prohibited on iOS and iPadOS, but of course there's way too much money at stake for these companies to pass it up.
Mysk points out that Apple is going to start requiring developers to declare reasons for using any APIs that return unique device signals in Spring of this year. Hopefully that helps reduce the amount of tracking these companies are able to do using sneaky tricks like this. We're not confident, though, because as we said, there's an immense amount of money at stake from user fingerprinting—and some of it comes from the US government.
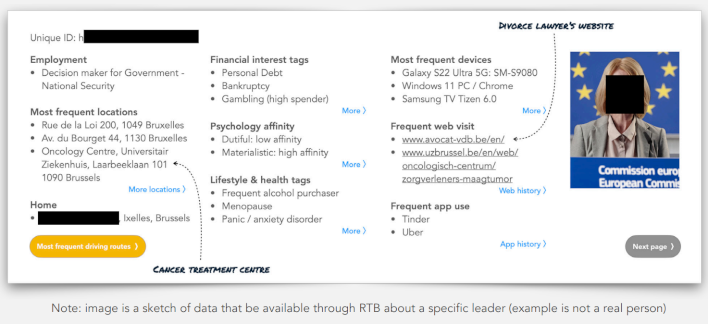
According to a report from Austrian security research institute Cracked Labs, Patternz is tracking over five billion people, including children. It does this using "Real-Time Bidding" (RTB) data. RTB is an advertising technology where advertisers bid in real-time on individual ad impressions, and it relies heavily on profiling users to understand what advertisements are likely to land with them.
The data included in these profiles can include almost anything, from a few data points about a specific smartphone user all the way to a detailed individual listing with personal information, known contacts, and even highly-specific location data accurate down to a few meters. Patternz collects this data from RTB companies like Google and X and then sells this data to third parties, including, as it turns out, the United States federal government.

In a letter to Senator Wyden, NSA Director Paul Nakasone refers to this data as "commercially-available information" (CAI), and while acknowledging that the NSA does indeed collect and purchase CAI, he also says that the information "provides significant intelligence value to the U.S. Intelligence Community, including NSA." According to Nakasone, the agency "takes steps to minimize the collection of U.S. person information". Right.
In response to these admissions, Senator Wyden has taken his case to Avril Haines, who is the Director of National Intelligence. In a public letter dated January 25th, Wyden calls upon Haines to hold the NSA and other agencies to the standards for legal data sales as established by the FTC. He also asks Haines to direct each US intelligence community element under her purview to clean up their databases of personal data on US citizens, purging any information that doesn't meet the FTC's standards.
It remains to be seen if Haines will agree to Wyden's terms, but that's neither here nor there for most of us. On a personal scale, in practical terms, it seems that if you want to limit how much information corporations and governments have about you, better keep that smartphone turned off whenever possible. By the way, the report from Cracked Labs [PDF] is quite alarming and worth a read if you're interested in your digital footprint and privacy matters in general.