Ghastly GhostRedirector Gang Is Hijacking Windows Servers For Google SEO Tricks
The first tool, Rungan, places a backdoor on the targeted machine that allows the hackers to set up shop and continue to deploy additional malware to reestablish a foothold if Rungan itself is discovered and shut down. The other tool, Gamshen, is a malicious Internet Information Services (IIS) module that modifies the response the infected server returns to Googlebot.
GhostRedirector isn’t just using custom tooling to compromise servers, though. The group is also taking advantage of publicly known exploits such as EfsPotato and BadPotato, which gives the attackers the ability to create new user accounts with administrative privileges. These user accounts can be leveraged to deploy the tooling the group uses to commit the SEO fraud.
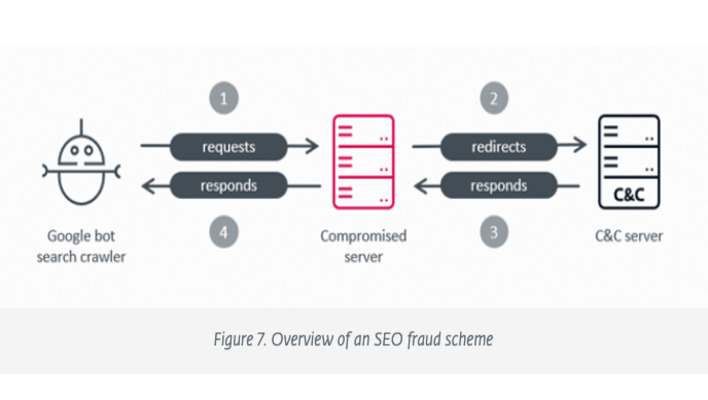
Once the hackers have established a foothold, the infected server passes along requests from the Googlebot engine crawler to a server the group controls. This command-and-control server then sends a response to the infected server, which is ultimately passed along to Googlebot. The response will contain information pointing the crawler to a third-party website instead of providing information from the legitimate site hosted on the compromised server.
Thankfully, a user visiting a website that has been affected by this campaign shouldn’t be negatively impacted. For now, GhostRedirector is only looking to compromise search engine results, not deploy malware to unsuspecting users.
The ESET researchers have already reached out to those whose Windows servers might have been hit by GhostRedirector. Hopefully these servers can be updated and have the infection removed to prevent further damage.

