Researcher Claims Windows 11 Secure Boot Is Broken On Hundreds Of MSI Motherboards
Manufacturers of computer hardware also work to comply with Microsoft’s new security standards by including and enabling TPM 2.0 and Secure Boot by default. However, according to new findings by a security researcher, the default Secure Boot settings on MSI motherboards are effectively tricking Windows 11 and potentially giving users a false sense of security.
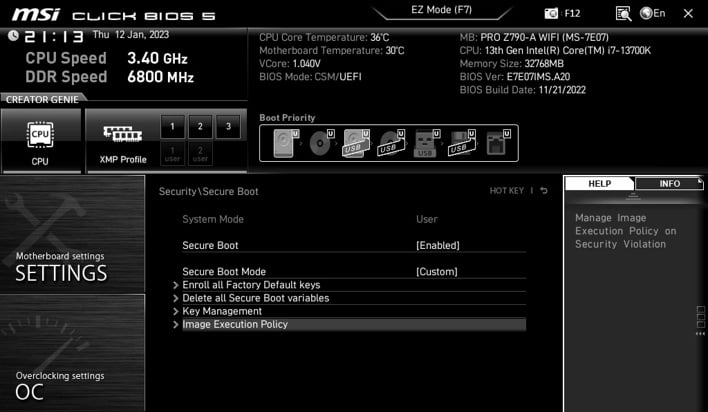
Those with MSI motherboards may have noticed that Secure Boot is listed as enabled by default, both in the BIOS and in Windows. However, as Dawid Potocki recently discovered, these indicators aren’t sufficient to verify that Secure Boot is functionally properly. As you can see in the image above, while Secure Boot is marked as “Enabled” in the BIOS, Secure Boot Mode is set to “Custom,” activating a group of sub-menus with further Secure Boot settings.
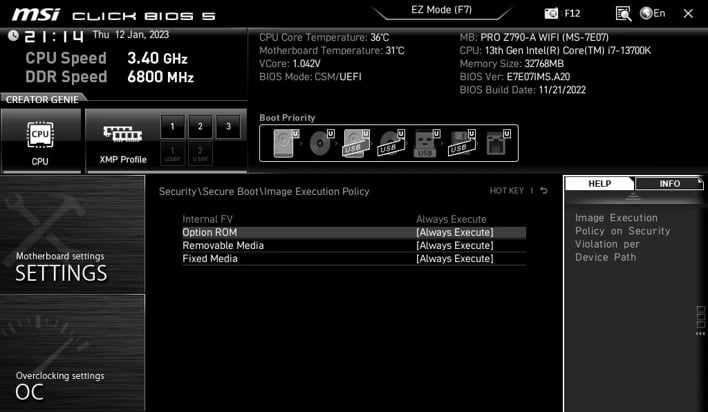
However, according to Dawid Potocki’s research, the default configuration for a wide range of MSI motherboards has all of these rules set to “Always Execute.” This option effectively bypasses Secure Boot, as the system will launch any software at boot regardless of whether it bears a signature that Secure Boot recognizes as safe. Thus, many MSI motherboards seem to appease the Windows 11 security requirement by marking Secure Boot as “Enabled,” while operating according to rules with the same effect as if Secure Boot were disabled.
This default configuration is a boon to threat actors, enabling them to implant persistent malware on compromised systems without needing to bypass Secure Boot with an exploit. Unfortunately, it doesn’t seem that MSI is willing to acknowledge this problem, as Potocki’s attempts to contact the company have so far been ignored. That said, users can patch up this security hole themselves by entering the BIOS and changing the “Always Execute” rules to “Deny Execute.” Since the full list of affected MSI motherboards is hundreds of lines long, we won’t copy it here. We encourage those with MSI motherboards to check the list on GitHub for their model numbers or enter the BIOS and audit the Secure Boot settings themselves.

