Stealthy MoonBounce UEFI Malware Alarmingly Infects Your BIOS To Execute Malicious Code
In 2021, a Kaspersky product called “Firmware Scanner” discovered a Unified Extensible Firmware Interface (UEFI) firmware compromise through a single component in the code that was inspected. This compromise allowed attackers to tweak the execution flow of the machine’s boot sequence, allowing for the introduction of malicious code. This code would then live on the flash memory where the firmware resided, thus allowing the code to persist through a drive format or full drive replacement.
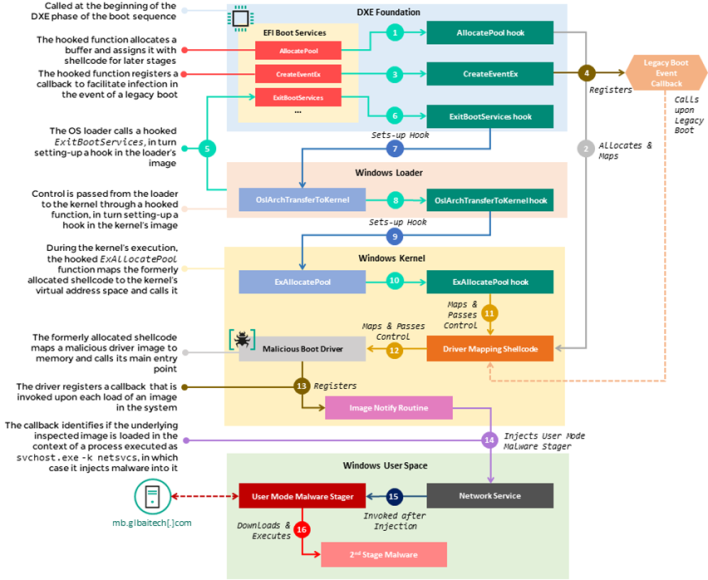
This infection chain worked by leveraging the CORE_DXE portion of the firmware, which is called during the Driver Execution Environment phase of the boot sequence. As a part of this phase, the CORE_DXE loads up a set of memory locations to routines that are a part of this component and can be called by other DXE drivers in the boot sequence. The infection begins when several functions within the memory location table are intercepted prior to being executed. The flow of these functions is then diverted to attacker-controlled code appended to the CORE_DXE image, which begins a multistage process wherein malicious code is spread throughout the CORE_DXE image to other boot components during the boot sequence.
Once the malicious code makes its way to the Windows kernel, it deploys malware by injecting it into a svchost.exe process after the operating system is started. Then, this malware reaches out to a command-and-control URL where it tries to get further payloads to run in memory. You can see how this process works in the diagram above, which outlines the process in more detail.
According to Securelist, who initially reported on the matter, this firmware rootkit was only detected in a single case alongside several other malicious samples in the same network range. Moreover, other malware was reaching out to the same command-and-control infrastructure from the network of an “organization in control of several enterprises dealing with transport technology.” Of course, all of this is to say that the average person is not at risk, and this work, which seemingly tied back to Advanced Persistent Threat (APT) 41, Earth Baku, or SparklingGoblin, is part of an espionage operation.
Despite this apparent limited scope of targets, Securelist warns that people should keep their UEFI firmware up to date and verify BootGuard is enabled if applicable. Furthermore, it is suggested that Trusted Platform Modules be enabled, and anti-malware products that can look into firmware should be used for added security.


