Website Hacking Campaign Is Infecting Unsuspecting Chrome Users With Malware
This is another issue that can be easily prevented using smart computing habits though don't be too hard on them when or if you receive that panicked text message. According to the folks at NTT Security, an IT service management company in Japan, hackers are actively compromising legitimate websites with malicious JavaScript code in an effort to target Chrome users.
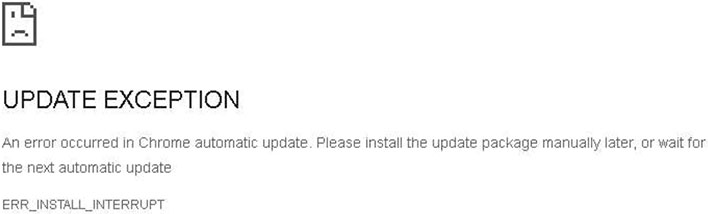
When a Chrome user visits a site that's been compromised in this manner, it displays a fake error message and instructs the victim to manually install an automatic update that is automatically downloaded as a ZIP file. It's not an actual an actual Chrome patch, of course, and instead the contents of the ZIP file installs a Monero miner onto the victim's PC.
"From around November 2022, an attack campaign that defaces legitimate websites and distributes miners has been observed. It displays a fake page that mimics the Google Chrome error page and uses social engineering to trick the user into executing malware. Some of the websites that have been defaced include Japanese websites, and the impact is widespread and serious. It may continue in the future, so be careful," NTT warns.
It's not clear how widespread this campaign, though BleepingComputer says it discovered multiple sites that have been hacked in a such a manner, including adult sites, blogs, news pages, and online stores. It's also tricky to try and block this behavior at the source via blacklisting. That's because the malicious scripts use the Pinata IPFS (InterPlanetary File System) service to hide the origin server hosting the files.
As part of the installation routine, the miner edits the system registry to exempt itself from Windows Defender scans. It also disables Windows Update and initiates other mechanisms that could further hinder a PC setup from thwarting malware threats.
Even if stumbling upon a compromised website, this can all be avoided by sending that ZIP file to the recycle bin. But again, less savvy users might assume it's a legitimate update.