Evasive Sturnus Malware Can Take Full Control Of Infected Android Devices
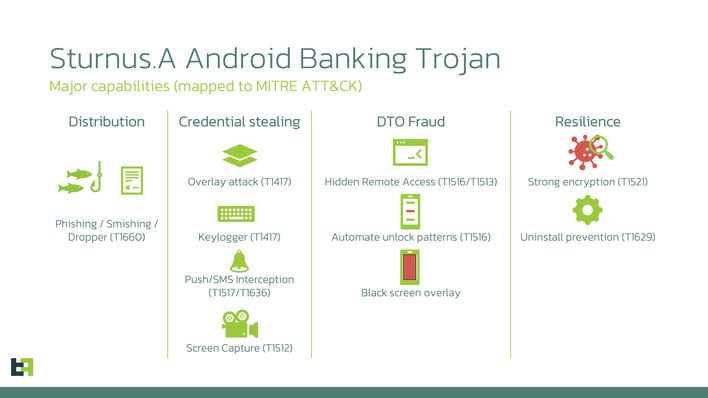
Moreover, the threat actors behind Sturnus use control of a device’s display to defraud unsuspecting victims. It’s able to black out the screen while while it works in the background to commit fraudulent transactions, enabling the theft of a victim’s funds without them ever noticing.
This malware is especially effective because it takes measures to ensure that it can evade detection by taking advantage of Android Device Administrator privileges. This allows attackers to keep tabs on password changes, lock screen activity and even prevent a user from revoking its administrator privileges. That makes this infection hard to root out once it takes hold.
Thankfully, Sturnus hasn’t seen mass deployment, with only a small number of victims so far. These victims were tricked into installing the malware through traditional e-mail phishing as well as its SMS-based equivalent, "smishing." While the impact has been limited, the researchers state that this is likely a precursor to a more widespread campaign in the future.
This is yet another example of malicious actors abusing Android users’ ability to sideload apps. It’s always recommended that users stick to known and trusted sources when installing apps, with the Google Play Store being the safest bet—though not even that is completely clean. Try to exercise your best judgement when choosing apps to install; just because it's approved by Google doesn't mean it's safe.