Sinister AXLocker Ransomware Adds Insult To Injury By Stealing Your Discord Account
Ransomware is a growing cause for concern in the information security field. Just last week, the Federal Bureau of Investigation (FBI) and other US government agencies issued a joint cybersecurity advisory warning cybersecurity professionals about the Hive Ransomware gang, which has stolen a total of $100 million from over 1,300 organizations. Two weeks before the publication of this advisory, the White House convened the second International Counter Ransomware Summit. Leading up to the event, a senior Biden administration official warned that the growth of ransomware attacks is outpacing the United States’ ability to combat them.
This growth is driving new innovations in the ransomware space, with Android malware developers trying to get in on the action by adding ransomware capabilities to their malicious software. An already established ransomware gang is also experimenting with the use of data corruption in place of data encryption. The addition of a Discord account-stealer, as seen in AXLocker, marks further experimentation among ransomware developers.
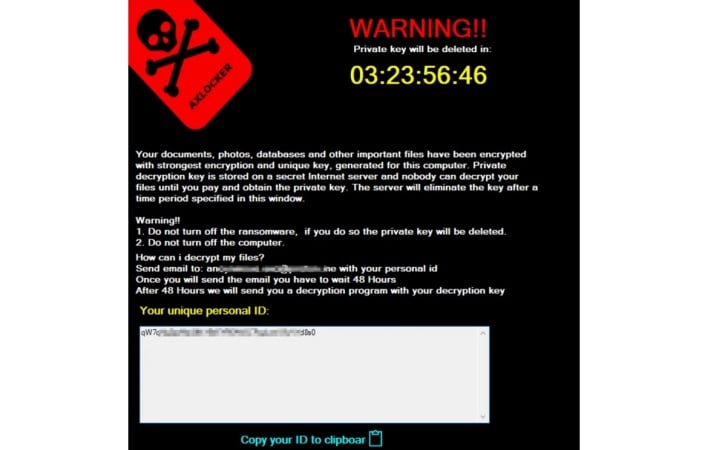
Once AXLocker has completed all its nefarious tasks, it opens a window informing the user that the files on the affected system have been encrypted with a private key. In order to obtain this private key and decrypt one’s files, the ransom note instructs the user to contact the threat actor and pay a ransom fee within a set time limit. A timer near the top of the window counts down the remaining time before the private key is deleted. The ransom note makes no mention of any stolen Discord authentication tokens, leaving victims oblivious to the act of theft perpetrated by the ransomware. Otherwise, victims might know to immediately change their Discord passwords to invalidate the stolen login tokens.

