Security Report Exposes A Sinister Evolution Of Ransomware Gang Extortion Tactics
Historically, ransomware works by infecting a victim’s computer and encrypting all the files with a key known only by the threat actors behind the ransomware. Without this key, the victim can’t decrypt and read any of the files on the computer. The threat actors then extort the victim by demanding payment in return for decrypting the files. However, in more recent years, ransomware has evolved to facilitate a kind of double extortion in which the threat actors both encrypt and exfiltrate victims’ files. Then, in addition to demanding a ransom for file decryption, the threat actors also threaten to publish the exfiltrated files on the internet.
Developing ransomware that utilizes encryption can be difficult. Threat actors are increasingly becoming affiliates of ransomware developers and pay them a percentage of their profits, rather than developing their own ransomware. However, encryption can be an unreliable ransomware technique, as security researchers can leverage bugs in ransomware to decrypt victims’ data. Internal disagreements between members of a ransomware gang can also drive members to leak the encryption key, once again giving security researchers the ability to decrypt victims’ data.
Ransomware double extortion is usually aided by a dedicated leak site (DLS) on the Tor network where threat actors publish both their threats and victims’ data, in the event that the victims don’t pay the ransom. These dedicated leak sites are run by ransomware gangs that operate according to the ransomware-as-a-service (RaaS) model. These gangs develop ransomware and distribute it to various affiliate actors, who in turn use this software to encrypt and exfiltrate victims’ data. The affiliates then must pay a percentage of all ransom profits to the gang that develops the ransomware and publicizes double extortion threats to its DLS.
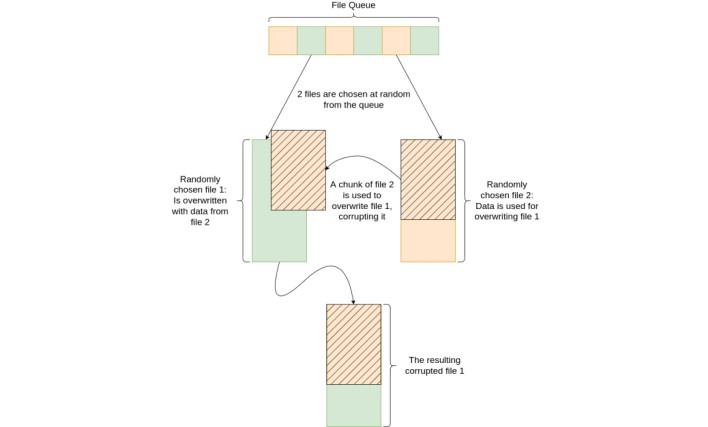
Unlike encryption, this corruption process doesn’t use a key that could reverse the process, meaning the corrupted files are rendered permanently unreadable. This kind of data corruption proves advantageous for the ransomware affiliate actors whose exfiltrated copy of the files remains uncorrupted. Rather than offering to decrypt files on victims’ computers for a price, the threat actors can instead extort victims by charging victims a ransom fee for the chance to download the uncorrupted copies of their files from the threat actors.
If ransomware were to shift to from data encryption to data corruption, threat actors wouldn’t have to worry about security researchers decrypting victims’ data. Additionally, threat actors could use common data exfiltration and corruption tools for free, rather than paying a percentage of their profits to ransomware developers. These advantages may drive threat actors toward corruption over encryption as a ransomware technique. That said, cybersecurity researchers have so far spotted only one instance of corruption used in place of encryption, so we have yet to see whether this substitution becomes a trend.

