MortalKombat Ransomware Chains Multi-Stage Attacks To Score A Fatality On Your Data
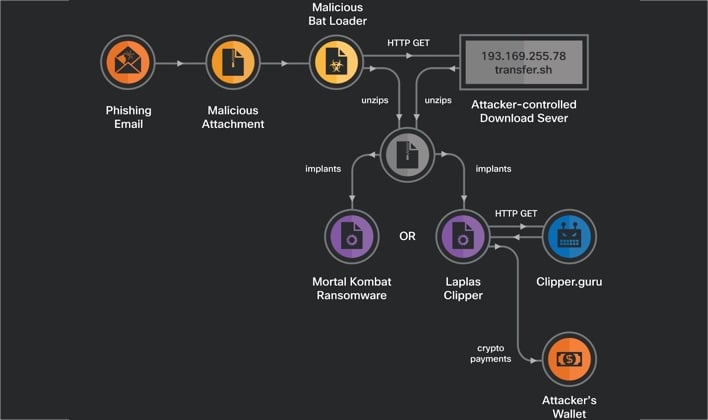
The file in question is a batch file that executes a malicious script. The researchers have found two different versions of this batch file: one that downloads and executes the MortalKombat ransomware and one that downloads and executes the Laplas Clipper malware. The latter malware is a clipboard stealer, but, rather than simply exfiltrating everything copied to victims’ clipboards, the malware quietly monitors the clipboards of infected systems for cryptocurrency wallet addresses.
Once Laplas Clipper detects a wallet address in a clipboard, the malware quickly uploads this address to a server controlled by the threat actors and receives back a similar-looking address tied to the attackers’ wallet. The malware then overwrites the original wallet address in the clipboard with the new address. Unsuspecting victims then paste this second address, thinking it to be their own. However, any funds transferred to this address end up in the threat actors’ wallet, rather than the victim’s.
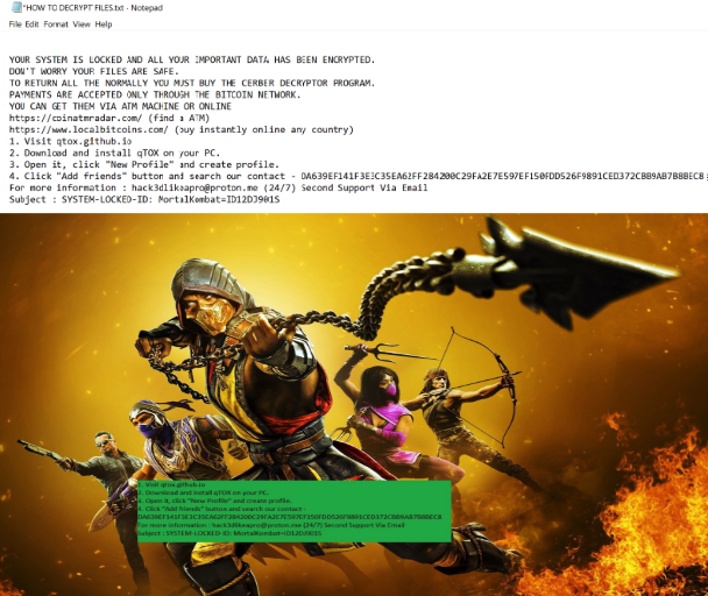
Once the damage is done, MortalKombat executes its finishing move, which is to replace the desktop background with ransom instructions overlayed on Mortal Kombat 11’s cover art. The ransomware also drops a ransom note text file. Both the desktop background and ransom note instruct victims to download and install the Tor-based qTOX instant messenger to communicate with the threat actors. The ransom note also informs victims how to purchase cryptocurrency for the purpose of paying the ransom fee. So far, it appears that the threat actors behind this campaign are limiting their extortion to the decryption of files stored locally on victims’ machines, rather than attempting to perform double extortion by threatening to publish victims’ files to a dedicated leak site.

