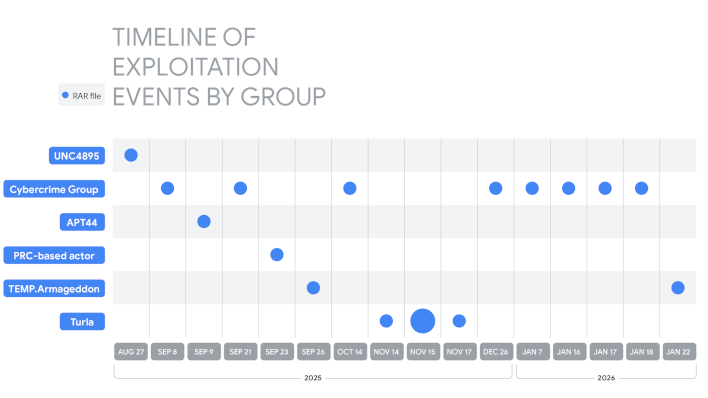
Remember the
WinRAR path handling exploit we reported on back in August? According to Google, that same flaw, officially dubbed CVE-2025-8088, is still being actively exploited, even though versions of WinRAR newer than v7.12 have been patched. Google's recent blog post on the exploit activity provides a timeline of exploits across six different groups, with a number of them (UNC4895, Cybercrime Group, and APT44) operating on behalf of Russia against Ukraine. There's also a PRC-based actor (Chinese) using the exploit to deliver POISONIVY malware, and miscellaneous attacks across Indonesia, Latin America, and Brazil. This is an international threat being leveraged in all sorts of ways, and users who aren't keeping their operating systems and copies of WinRAR up-to-date are all vulnerable to attack.
Unlike
CVE-2025-62221 and CVE-2025-6222, which have also already been patched, CVE-2025-8088 has proven surprisingly prominent. Google notes that "When a reliable proof of concept for a critical flaw enters the cyber criminal and espionage marketplace, adoption is instantaneous, blurring the line between sophisticated government-backed operations and financially motivated campaigns. This vulnerability's rapid commoditization reinforces that a successful defense against these threats requires immediate application patching, coupled with a fundamental shift toward detecting the consistent, predictable, post-exploitation TTPs." In layman's terms, this means that the current generation of cyber crime has such a high financial incentive that common crooks and governments alike are driving the adoption and use of these exploits more quickly than ever, and that practices for both users and developers will need to change in order to offset these risks,
especially for those dealing with confidential data.
Google's
full blog post provides more details on the matter, including a long list of known file indicators for the exploit. For most users, we advise
updating WinRAR as soon as possible, and making the switch to Windows 11 or Linux from Windows 10 if you haven't already.