Microsoft Warns This Sophisticated Mac Trojan Is Getting More Sinister
According to Microsoft, the malware infects its victims’ computers by impersonating legitimate software or bundling itself with legitimate software, tricking users into installing it. When it first began appearing on devices, this basic information-stealer originally did very little once installed, until about two months later. Sometime between January and February of 2021 the malware gained the ability to download and install secondary payloads from public cloud infrastructure, putting victims’ computers at risk of developing further infections.
Then, in March 2021, the malware received a third update enabling it to bypass MacOS’ Gatekeeper security feature. Files downloaded from unknown sources are marked with a quarantine designation that forces Gatekeeper to block said files from launching and display pop-up warnings telling users that they can’t open files from unidentified developers. However, with the March 2021 update, UpdateAgent gained the ability to remove the quarantine designation from secondary payloads.
At the same time, the malware began creating its own PLIST file and adding it to the LaunchAgent folder, causing the malware to automatically run upon user sign-in. In August 2021 this behavior was changed so that UpdateAgent began placing its PLIST file in the LaunchDaemon folder rather than LaunchAgent, permitting the malware to inject persistent code that ran as root. Running code in this way makes the malware more difficult to detect, because it runs as background processes with which users don’t interact. The August 2021 update also enabled the malware to scan and collect additional information about infected devices, namely System_profile and SPHardwaretype information, revealing devices’ serial numbers among other things.
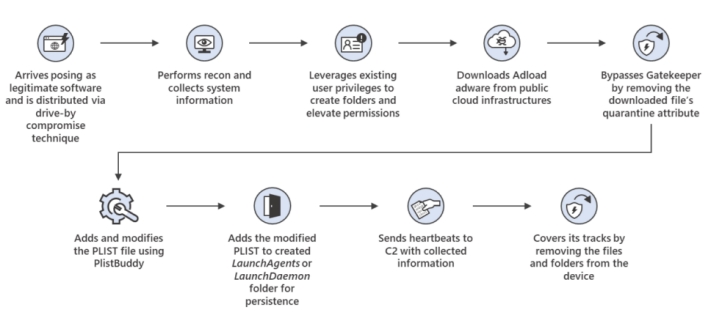
The above image shows UpdateAgent’s attack chain as of October 2021, which is significantly expanded compared to the UpdateAgent that first appeared a year earlier. By detailing this particular malware’s development over the course of a year, Microsoft highlights the ability of malware to become more complex and dangerous over time. The company says in its blog post that other info-stealing trojans follow similar progressions. You can check out the blog post if you want to learn about the specific steps that UpdateAgent takes to infect a device.

