Urgent Microsoft Office Security Alert: All Applications Vulnerable To Homograph Attacks
A homograph attack makes use of what are known as homoglyphs. Homoglyphs are letters or characters that appear identical, or close to it, such as the lowercase “L” and the uppercase “i” characters. Attackers can leverage these sorts of similarities by directing victims to websites with URLs that appear legitimate, but are actually spelled slightly differently. For example, victims might think they are visiting google.com, but they’re actually visiting g00gle.com. In a homograph attack, the attackers control this misspelled domain and use it to distribute malware or steal victims’ login credentials by presenting users with a website that mimics the website located at the legitimate domain.
An IDN homograph attack is a particular kind of this form of attack that leverages letters from other alphabets. Domain names were originally limited to Arabic numerals and the Latin alphabet, which are used by the English language. However, there are many languages that use letters not found in the Latin alphabet, so a new standard eventually came about for registering domain names with non-Latin characters. Domain names registered in this way still use Latin characters underneath, but they can be displayed with non-Latin characters.
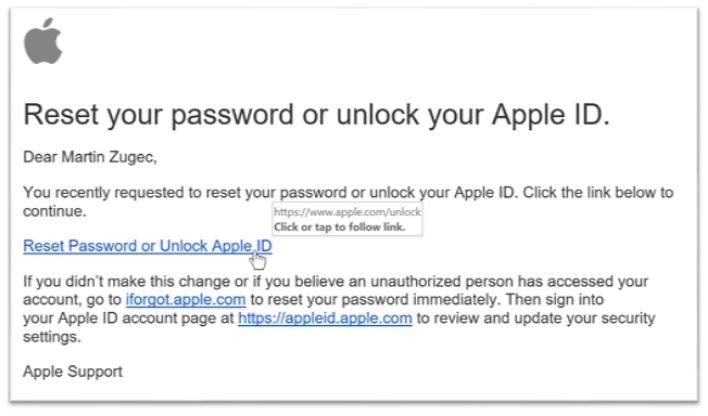
Some web browsers and email clients try to protect against IDN homograph attacks by displaying internationalized domain names with Latin characters, rather than non-Latin characters, so that users can distinguish between the legitimate apple.com domain and the xn--pple-43d.com domain name that appears as “аpple.com” when rendered with Cyrillic characters. However, researchers at Bitfender have highlighted the fact that the full Microsoft Office suite of applications, including the Outlook 365 email client, render IDNs with non-Latin characters, leaving users vulnerable to IDN homograph attacks. The image above shows xn—pple-43d.com rendered as “аpple.com” in Oulook 365.
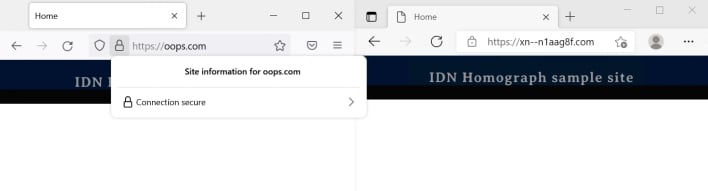
However, Microsoft’s own Edge browser is less forgiving of IDNs, as you can see in the image above, where Edge displays xn--n1aag8f.com in Latin characters, while Firefox displays this domain name with non-Latin characters as “оорѕ.com.” Thus, one might think that Microsoft would consistently render IDNs with Latin characters across its different applications, including the Microsoft Office suite. That said, Edge is built on Chromium, so Edge may simply employ the IDN homograph attack mitigation built into Chromium, rather than rendering IDNs in Latin characters as specified by Microsoft developers.

