Microsoft’s
Azure Active Directory has some neat features built-in, and it is always expanding. Yesterday, the Azure team implemented a way to detect “one of the most popular attacks, accounting for more than a third of account compromise in organizations.” This attack is called password spray, and by now using machine learning,
Microsoft can detect patterns and alert organizations to this attack.
Password spray is a “low and slow” form of attack, where “bad actors try a few common passwords against many accounts from different organizations.” This method of testing passwords over several days can go undetected as logins can come from thousands of IPs and can get lost in regular login attempts. As Alex Weinert of Microsoft writes, “A customer might only see one or two failed logins happen from these types of attacks once a day, so the attacks get lost in the noise of normal login patterns. They also bypass traditional protection like password lockout and malicious IP blocking.”

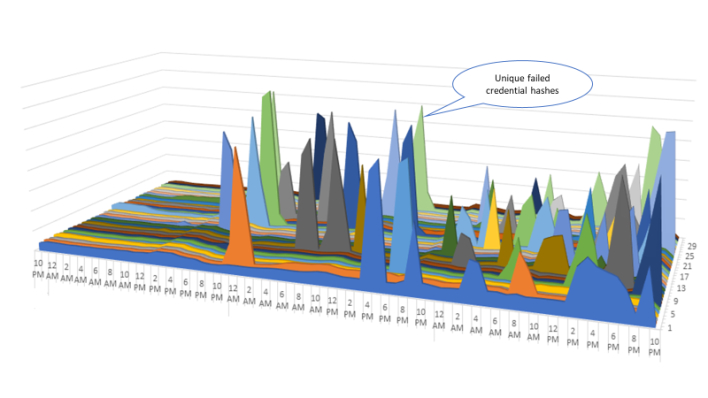
Microsoft started to look across the entire system and was able to detect patterns, though. Through the graph seen above, they could see spikes in password hashes being used. Weinert says that “this lens extends our detections beyond traffic from a set of IP addresses (a few of these attacks have originated from millions of IP addresses) and instead correlates the patterns of authentications the bad actors are attempting.” This lens, while useful, was not enough for the team, though. The data scientists at Microsoft decided to use the patterns and data to train a
machine learning system to detect when password spray attacks occur. With 98 percent precision, Weinert explains that “if this algorithm says an account fell to password spray, it’s almost certain that it did.”
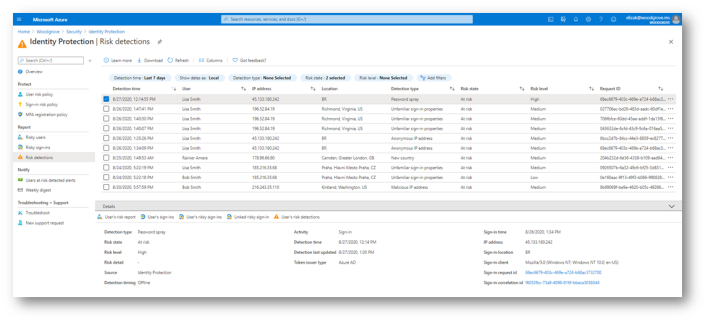
The data and machine learning implementation are incredibly useful for organizations that have much to lose if an account is compromised. If an account were to fall, admins could know much more quickly to secure their network. Furthermore, you can use the data and output from the system to “automate processes in Azure AD Conditional Access, in Azure Sentinel, or through the APIs for anything you can imagine.” With this, Microsoft makes
cybersecurity easier to maintain and better than ever with its new Azure AD features.