Microsoft Uncovers Windows And Linux Botnet Used To DDoS Minecraft Servers
Threat actors, or more likely script kiddies, are always looking for new ways to wreak havoc on the world, and what better way than to attack the gaming world? The botnet, called MCCrash, originates from malicious software embedded in software cracking tools for Windows devices, where it will then spread to Linux or IoT devices. It then spreads by attempting to use default credentials on internet-exposed SSH-enabled devices like IoT devices.

Interestingly, the researchers note that this extensive botnet has largely captured Russian-based devices and is probably part of a service that is sold on dark websites or forums. Whether or not this is a DDoS-as-a-service platform, it works to take down Minecraft Java servers by sending specially crafted packets to exhaust the resources of the Minecraft server. Specifically, this leverages the Log4j 2 library and its env variable to bring down the systems but is unrelated to the Log4Shell vulnerability.
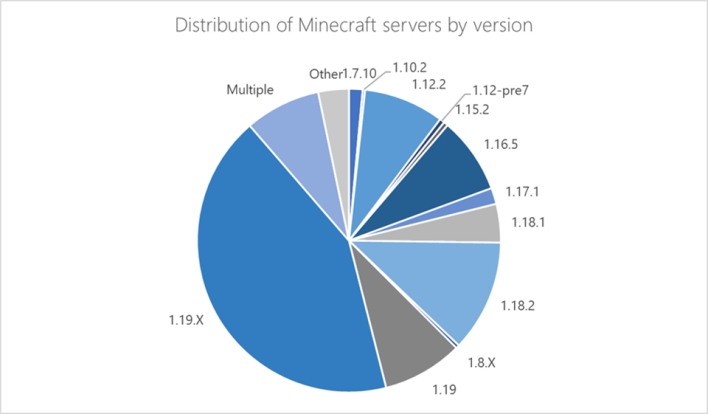
Researchers also note that the malware used for the botnet is hard coded to target Minecraft server version 1.12.2. In theory, though, it would work from Minecraft server version 1.7.2 to 1.18.2, which encompasses many Minecraft servers worldwide. Thankfully, a change made in Minecraft 1.19 prevents using these commands and capabilities.
In any event, this botnet is particularly dangerous because of its use of IoT devices which lowers its detectability and increases impact, according to the researchers. However, because the malware was hardcoded to only attack Minecraft version 1.12.2, its scope is significantly more limited, though that could change or be copied by another botnet in the future.


