Oh Great, Hackers Are Using Stolen NVIDIA Certificates To Sign Windows Malware
LAPSUS$ claims to have stolen 1TB of data from NVIDIA servers and has purportedly stolen 204GB of data from Samsung as well. This stolen data includes propriety source code, and a full leak of this data could be disastrous for both NVIDIA and Samsung. LAPSUS$ has leaked just 20GB of the supposed 1TB of NVIDIA data, and this relatively small leak is already proving to be harmful, not only for NVIDIA as a company, but also for its employees and now unrelated victims of malware.
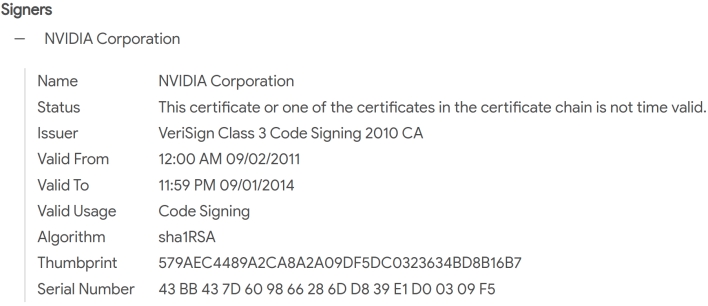
Security researchers have already discovered multiple cases of malware in the wild that has been signed with a leaked NVIDIA certificate. The certificate enables malware to masquerade as legitimate NVIDIA software, bypassing important Windows safeguards against malicious software.
Microsoft will hopefully respond to the malicious abuse of these leaked certificates by adding them to its certificate revocation list, but doing so could block legitimate NVIDIA drivers. Thus, it might take some time before we see these leaked certificates lose their functional validity, and bad actors will continue to use the leaked certificates to load malware on Windows machines in the mean time.
For now, David Weston, Vice President of Enterprise and OS Security at Microsoft, has a Twitter thread on how to use Windows Defender Application Control policies to limit what NVIDIA drivers Windows can load. Florian Roth, a detection engineer, has also created a rule for YARA, an open source malware detection tool, that detects the two leaked NVIDIA certificates.

