NVIDIA Hackers Now Threaten Samsung Source Code Leak For Biometrics, Bootloader, Knox And More
Recently, this same hacker group targeted NVIDIA, claiming to have stolen 1TB of data from NVIDIA servers, and was attempting to ransom it back for an unspecified amount. The hackers also claimed that NVIDIA took matters into their own hands by hacking them back, installing ransomware on their personal machines. The group is now demanding NVIDIA release it's graphics drivers and make them open source, otherwise it will release Verilog design source code on some of its most guarded trade secrets and future GPUs.
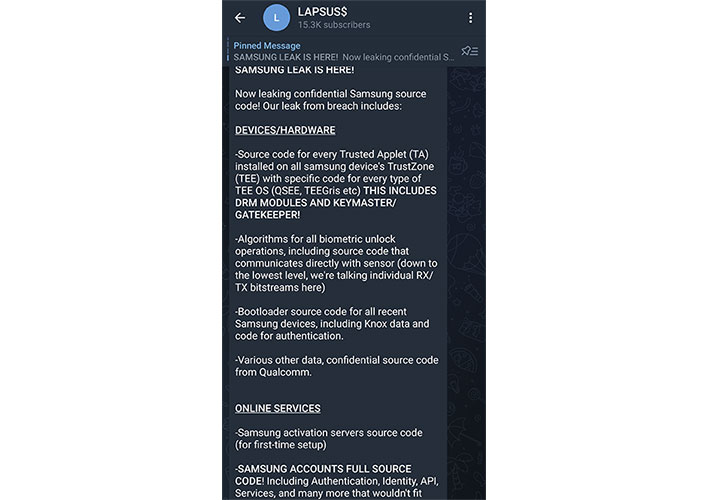
Now it appears the hacker group has been busy targeting other organizations beyond just NVIDIA, as it now claims to have released a large of amount of Samsung source code, according to messages it posted on its Telegram account yesterday afternoon at around 3:30 PM ET.
Of the most damaging drops of code they claim to be releasing is Samsung Knox data and code for its authentication system. Knox is Samsung's pride and joy when it comes to security for their smartphones. It is designed to isolate, encrypt, and secure your data, including confidential files, credit card transactions, passwords and health records. Samsung markets the security suite heavily to enterprise customers as well. So, if Knox proprietary code makes it out into the wild, it could spell disaster for a large number of people, businesses and of course Samsung.
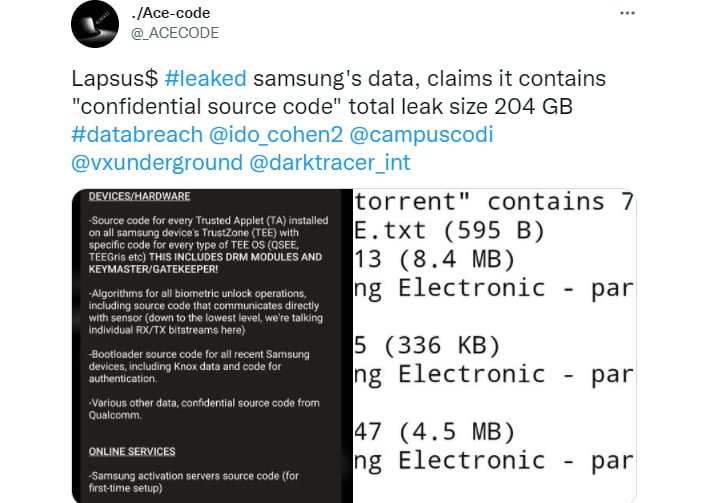
Another repository of data the hackers are claiming to have possession of involves source code for every Trusted Applet (TA) installed on all Samsung devices, as well as TrustZone TEE OS (QSEE, TEEGris etc). The hacker's post states this it includes DRM modules and keymaster/gatekeeper data as well.
The information being leaked is not limited to just Samsung apparently either, as the group also claims it will be sharing various other confidential source code from Qualcomm as well.
At the time of this publication, LAPSUS$ hosting servers were being hammered with people trying to download the files, which includes over 200GB of data. At one point it was showing a download queue time of over 7,000 days. The group says they are working on boosting server resources to help handle the load.
As with all stories of this nature, it is evolving and we will stay on top of any new developments. Keep an eye out here for updates and future coverage.