Hacker Behind Australia's Largest Data Breach Gets Cold Feet And Tries To Retract Leak
Hacker Claims Data From 11.2 Million Optus Customers Stolen
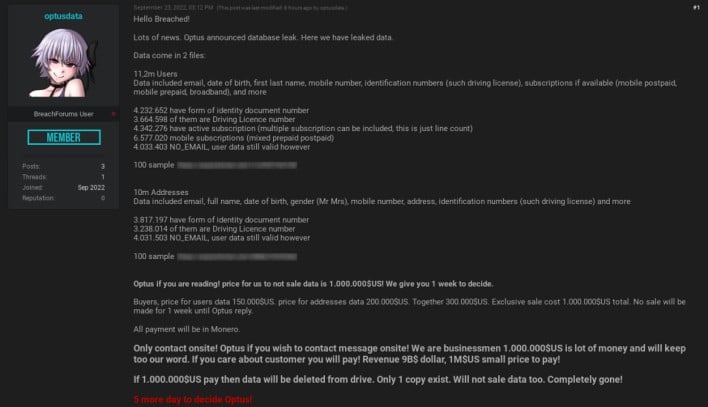
A day after Optus disclosed the data breach, an unknown actor posted to the hacking website Breach Forums under the name “optusdata.” The forum user started a thread in which he claimed to possess customer data stolen from Optus in the data breach. The owner and administrator of Breach Forums, pompompurin, replied to the thread saying he verified the authenticity of the user’s claims by speaking with him and viewing a sample of the data.According to the original forum post, the threat actor stole data pertaining to 11.2 million Optus customers. The post links to two samples of the data, which include names, dates of birth, email addresses, phone numbers, home addresses, driver’s license numbers, passport numbers, Medicare ID numbers, and subscription information.
Optus has since issued a statement indicating that 9.8 million customer records were exposed. However, the company also recently informed customers of Virgin Mobile and Gomo that their personal information was included in this data breach, and it’s unclear whether these customers are included in that 9.8 million. While Virgin Mobile and Gomo are both subsidiaries of Optus, not all of the company’s subsidiaries were affected. According to reporter Josh Taylor, Amaysim customers were not affected by this breach.
Optus Denies The Breach Was Due To "Human Error"
An unnamed “senior figure” within Optus told ABC News that the breach appears to have been the result of human error. More specifically, the internal Optus customer database was connected to an Application Programming Interface (API) that was exposed to the open web by way of “a test network which happened to have internet access.” This explanation of the breach was corroborated by optusdata, who spoke with reporter Jeremy Kirk on Breach Forums. Kirk shared screenshots from his conversation with the threat actor, who said that he accessed the database through an API found at an easily-guessable web address. This address seems to be legitimate, as it appears in GitHub repositories dating as far back as 2018.What’s more, optusdata told Kirk that the API endpoint was unauthenticated, meaning it was unprotected by any kind of login credentials. It’s possible that this API was protected by authentication in the past and only recently became unprotected prior to the breach. Optus appears to have responded to the data breach by taking the API offline. However, in correspondence with ABC News, Optus directly denied the claim that human error was at fault for the breach, with the CEO insisting that the company has “very strong cyber defenses.” Optus instead attributed the breach to a “sophisticated” cyberattack, but didn’t provide any additional details.
It isn’t clear that the threat actor attempting to extort Optus customers directly is the same actor as the one responsible for the data breach. An unrelated actor could have used the information released in the data samples to contact Optus customers in an attempt to scam them out of their money without any ability to follow through with the promise to erase their personal information from the stolen database.
Cold Feet?
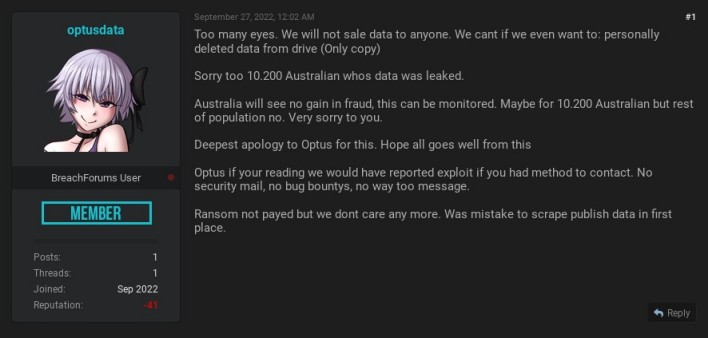
Regardless, almost all of the stolen data may have been deleted without either Optus or its customers paying a single cent. On Tuesday, optusdata deleted the original forum thread announcing the data breach and replaced it with a new thread announcing that the stolen Optus data won’t be sold or leaked to anyone. The post offers repeated apologies and states that the only copy of the stolen data has been deleted. Some Breach Forums users speculated that Optus ended up paying the ransom fee after all, but reporter Jeremy Kirk received confirmation from Optus that the company did not pay a ransom.A likely explanation for the sudden change of heart is that the threat actor began to feel the pressure of law enforcement. According to the forum post, the data breach drew too much attention, making it impossible to sell the data. This retraction came less than a day after the Australian Federal Police announced “Operation Hurricane” with the stated goal of identifying the cybercriminals behind the Optus breach and preventing identity fraud. The Australian government also reportedly called in the US Federal Bureau of Investigation (FBI) for help.
Some Irreversible Damage Is Done
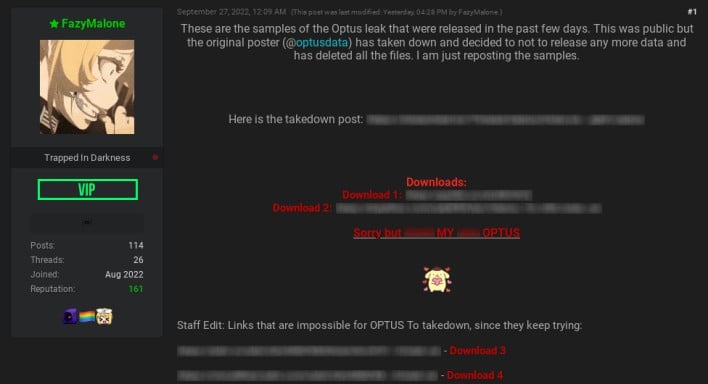
Unfortunately for a small subset of Optus customers, the data samples published in the original forum post live on. The samples continue to be available for download from another Breach Forums user who has reposted them in a new forum thread. These samples list the personal information of 10,200 Optus customers, putting them at risk of identity fraud.We also have no confirmation at this point that the larger stolen database was actually deleted, so Optus customers shouldn’t simply shrug off the data breach. The stolen database could show up at another time, so Optus customers should take precautionary measures. Fortunately, state governments are working to assist Australians affected by the breach, with many offering ways for people to more easily acquire new driver’s licenses. Optus has even pledged to pay driver’s license replacement fees for residents of New South Wales.
Beyond driver’s licenses, the Australian Minister for Foreign Affairs, Penny Wong, has sent Optus a letter requesting that the company cover the cost of new passports for customers affected by the breach. The Australian Federal Police also just announced a joint operation with all State and Territory police, the Australian Cyber Security Centre, the Australian Banking Association, IDCARE and the Customer Owned Banking Association. Named "Operation Guardian," the coordinated effort is intended to identify the 10,200 Optus customers whose information was leaked in the data samples and provide them with additional protections.