Google Takes Down Massive Malicious Proxy Network, Millions of Zombie Devices
If you're familiar with botnets, you already understand most of what a malicious proxy network is. A botnet describes a large number of compromised devices being used (often without the knowledge of their owners) for malicious purposes, i.e. password breaking and DDOS attacks. A malicious proxy network also involves a large number of compromised devices, and compromised networks specifically, where a broadband connection becomes the exit point for all kinds of unsavory traffic. This is how IPIDEA functioned, effectively masking criminal traffic in a sea of legitimate users.
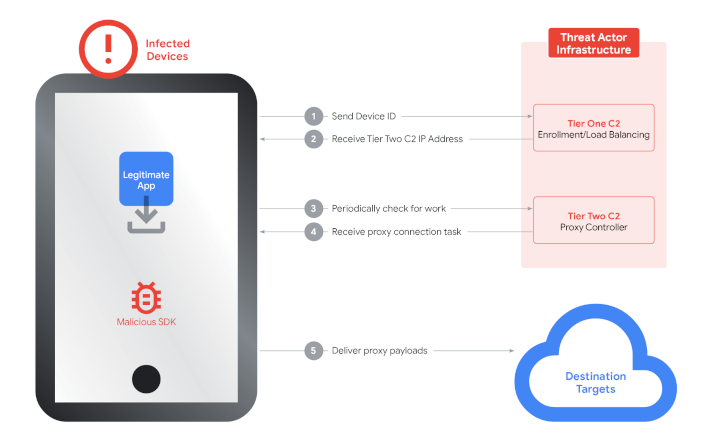
The full Google Cloud blog post details the warplan against IPIDEA, including lists of IOCs (Indicators of Compromise) and File Indicators. Google notes that while a major blow against IPIDEA's functionality has been struck, underworld efforts like these will continue exploiting legitimate users, networks, and devices without sufficient collaboration across the industry and accountability among proxy providers and app developers. So, stay vigilant, and remain wary of applications with no clear monetization path, especially those offering costly services (like VPN functionality, free premium video, etc).
Image Credit: Google, CodyHofstetter on WikiMedia Commons (CC 4.0 license)


