Google Exposes Startling Italian Hermit Spyware That’s Attacking Android And iOS
Technology firms such as NSO Group develop spyware and sell it to state actors all within the bounds of the law. These groups maintain that the spyware is for use by authorized government authorities only, but recent history seems to show that unintended actors have managed to deploy this kind of spyware. Last year, an investigation found that NSO Group’s Pegasus spyware had infected the phones of at least nine US State Department employees, leading NSO Group to launch its own investigation into this use of its spyware.
Now Google’s Threat Analysis Group (TAG) has discovered a different spyware campaign targeting Android and iOS users in Italy and Kazakhstan. Researchers at Lookout Threat Lab dubbed this spyware “Hermit” and attribute it to RCS Labs, which is an Italian spyware vendor. RCS prides itself on being “the leading European provider of complete lawful interception services.” The Hermit spyware has been deployed before, but this new campaign features a particularly alarming tactic.
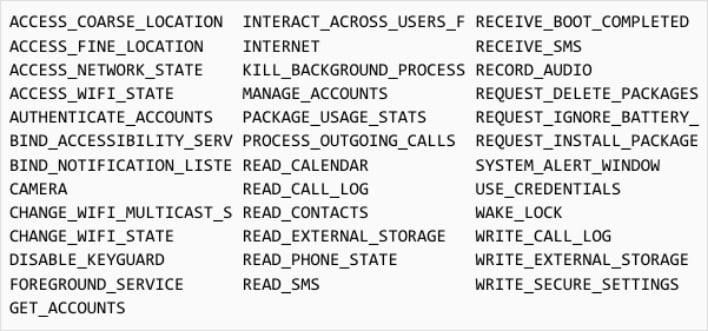
These malicious apps weren’t ever available on the Google Play Store or Apple App Store, but were instead side-loaded from websites controlled by the attackers. Once installed, the malicious iOS apps exploited at least six different security vulnerabilities, including two zero-day exploits. The malicious Android apps, on the other hand, didn’t directly exploit any vulnerabilities themselves, but requested access to a large number of permissions, as shown above, and communicated with the threat actors’ command-and-control (C2) servers. The Android apps could retrieve additional malicious payloads from the C2 servers and install them on infected devices.
Google has responded to this spyware campaign by warning all Android victims, implementing Google Play Protect changes, and disabling the Firebase Cloud Messaging projects that were being used as C2 servers. While we still don’t know who was behind this spyware campaign, all of the websites that distributed the malicious apps have since been taken down, so the campaign is hopefully over for now.

