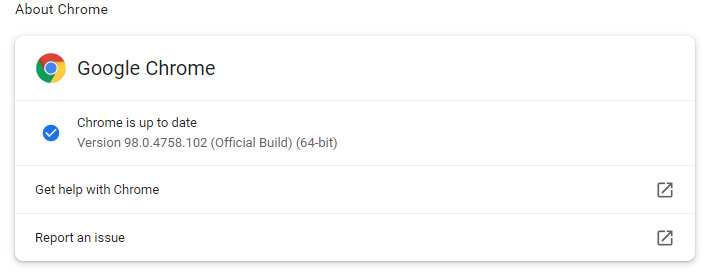
If you're using
Google's Chrome browser your Windows PC, Linux system, or Mac computer, be sure you have the latest version installed (version 98.0.4758.102). That's because the latest update contains several security fixes, including an emergency patch for a zero-day vulnerability that Google says is being actively exploited in the wild.
That specific vulnerability is listed as CVE-2022-0609 and unfortunately there is very little information about it at this time. Or fortunately, as
Google often holds off divulging the nitty-gritty details about such things until users have had a chance to apply the update. Otherwise, it just brings to attention another attack vector for hackers before the majority of users are properly protected.
It's simply described as a "Use after free in Animation" exploit, which was discovered and reported by
Adam Weidemann and Clément Lecigne from Google's Threat Analysis Group.
In total, the latest update includes 11
security fixes, over half of which are deem High in severity. The listed
bug bounties total $29,000, though the actual sum is higher—there are at least two bounties that are yet to be determined.
Google provided bare minimum details on most of them. They include...
- High: CVE-2022-0603: Use after free in File Manager. Reported by Chaoyuan Peng (@ret2happy) on 2022-01-22
- High: CVE-2022-0604: Heap buffer overflow in Tab Groups. Reported by Krace on 2021-11-24
- High: CVE-2022-0605: Use after free in Webstore API. Reported by Thomas Orlita on 2022-01-13
- High: CVE-2022-0606: Use after free in ANGLE. Reported by Cassidy Kim of Amber Security Lab, OPPO Mobile Telecommunications Corp. Ltd. on 2022-01-17
- High: CVE-2022-0607: Use after free in GPU. Reported by 0x74960 on 2021-09-17
- High: CVE-2022-0608: Integer overflow in Mojo. Reported by Sergei Glazunov of Google Project Zero on 2021-11-16
- High: CVE-2022-0609: Use after free in Animation. Reported by Adam Weidemann and Clément Lecigne of Google's Threat Analysis Group on 2022-02-10
- Medium: CVE-2022-0610: Inappropriate implementation in Gamepad API. Reported by Anonymous on 2022-01-08
Several of these are Use After Free bugs, which deal with memory corruption and are somewhat common among browser hacks. In this case, the UAF flaws affect File Manager, the Webstore API, ANGLE, GPU, and Animation, the latter of which
Google confirmed an exploit for "exists in the wild." That's notable, given it's estimated there are at least 3.2 billion Chrome users.
You can wait for an automatic update, but given the situation, you're best off forcing the issue. That's easy enough to do. Just click the three vertical dots in the upper-right corner to bring up the Chrome Menu and navigate to Help > Google Chrome. The browser will then check for an update and, if available, begin downloading it right away. Once finished, you'll need to relaunch Chrome.