Alarming Google Bug Exposes Account Phone Numbers Via Brute-Force Attack
To exploit this vulnerability, malicious actors need the victim's display name. However, since Google has removed users' display names from endpoints, accessing it without direct interaction with users should be impossible. Nevertheless, attackers can find a way around this by using sophisticated techniques to unmask a victim's display name. A security researcher demonstrated how this could be done in the video below.
Hackers will also need a hint about the victim's phone number, and they can easily get it by using the Gmail account recovery feature. For example, a number ending with 69 will have a masked phone number like ***********69. The display name and the phone number hint, used alongside an HTTP automation script and a valid botguard token, combine to leak a Google user's phone number.
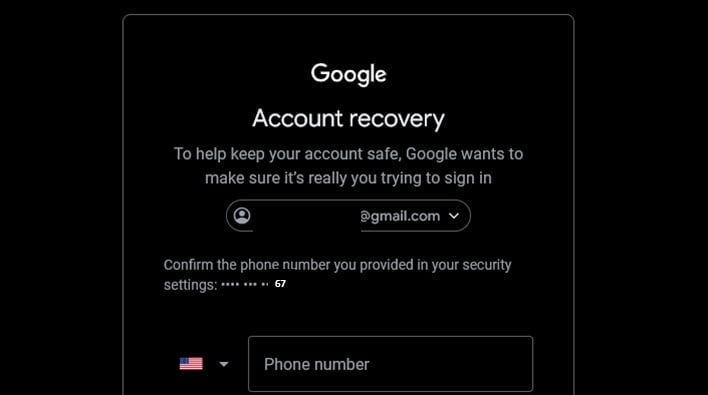
Google became aware of this vulnerability after it was reported on April 14, 2025. Initially, it downplayed it, claiming that the possibility of successful exploitation is low. After further examination, however, Google changed its stance, upgraded the flaw's severity to "medium severity" on May 22, 2025, and subsequently patched the vulnerability. A security researcher, BruteCat, discovered this vulnerability and published a post detailing how these vulnerabilities could be exploited.
Over the years, Google has responded to various privacy-related allegations against it by introducing various upgrades and security fixes to enhance user privacy, like when pushed out Gmail popups encouraging users to beef up their security with Enhanced Safe Browsing. Google also continually adds safety features to Chrome to protect users from an ever-evolving landscape of security threats.

