FIN8 Hackers Deploy Evasive White Rabbit Ransomware To Attack US Banks
There’s a new White Rabbit on the loose. While it does involve hackers, it’s got nothing to do with Neo. Instead, it’s yet another new ransomware family that recently appeared, targeting financial institutions.
Possibly a side operation of the FIN8 hacking group, White Rabbit was recently used to attack a US bank in December 2021. Trend Micro says the ransomware family behaves similarly to Egregor in how it hides its malicious activity.
White Rabbit’s payload executable actually requires a specific command-line password to decrypt its internal configuration and analyze what it’s doing. The payload itself is relatively small, only 100KB, and inconspicuous. It doesn’t have any notable strings or activity unless you know the decryption password to see its behavior.

Once deployed, White Rabbit targets data and then uses double extortion against the victim. In a double extortion scheme, the hacking group not only steals a company’s data, but also threatens to publish it. This puts much more pressure on the victim, since ransomware groups have proven recently they will definitely follow through on their threats.
Upon activation, the ransomware creates a note for each file it’s going to encrypt. It also terminates several processes and services, especially ones related to antivirus software. Once the damage is done, White Rabbit generates its ransom note.
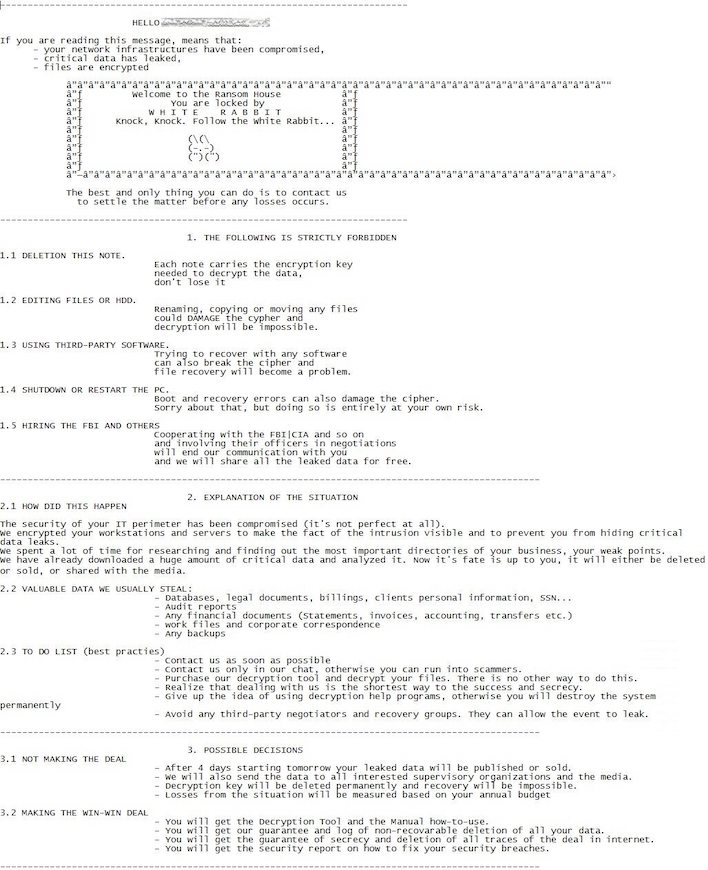
(Click to enlarge)
Trend Micro is still determining if FIN8 is actually involved with White Rabbit, or if they share the same creator. Researchers from Lodestone identified the malicious URL connected to the recent attack as being tied to FIN8.
The group also noted that White Rabbit uses a never-before-seen variant of F5 backdoor Badhatch, which is associated with FIN8. However, the files from that URL were no longer available during Trend Micro’s analysis.

