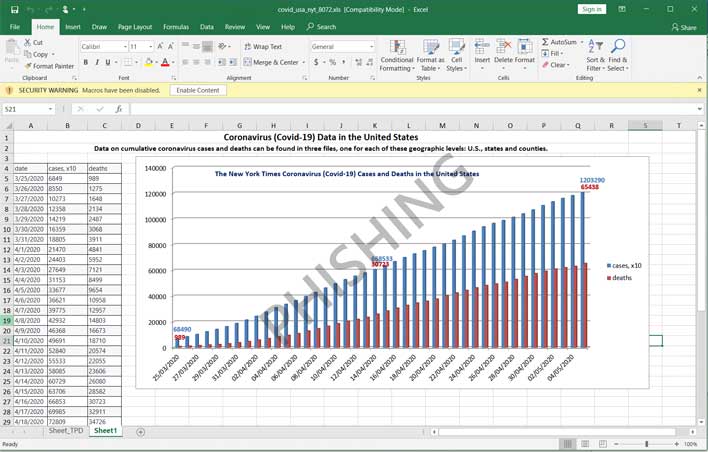
Dangerous Phishing Malware Runs Rampant With Coronavirus Data-Infused Excel Spreadsheets
Malware is something that computer users have fought since the dawn of the computer age it seems. Hackers who use malware to try breach networks and user data have evolved some pretty sophisticated methods as of late. Late this week, Microsoft Security Intelligence has announced via Twitter that it's tracking a "massive campaign" that delivers a malicious payload including the remote control access tool, NetSupport Manager, using emails with an attachment that contains malicious Excel 4.0 spreadsheet macros. The email campaign tries to fool users into opening an attachment that contains Excel pages that are COVID-19 themed and full of what appears to be statistics.
We’re tracking a massive campaign that delivers the legitimate remote access tool NetSupport Manager using emails with attachments containing malicious Excel 4.0 macros. The COVID-19 themed campaign started on May 12 and has so far used several hundreds of unique attachments. pic.twitter.com/kwxOA0pfXH
— Microsoft Security Intelligence (@MsftSecIntel) May 18, 2020
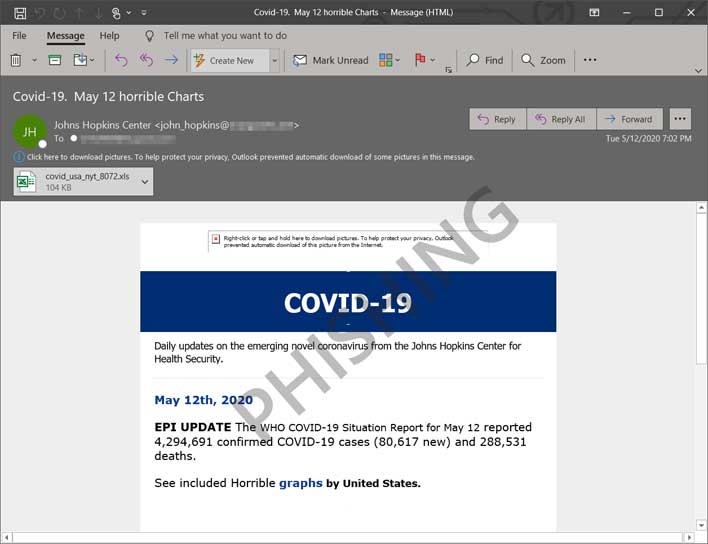
Microsoft reports that the emails claim to come from Johns Hopkins Center with the notation "WHO COVID-19 SITUATION REPORT". The file that contains the malicious macros has statistics on it that claims to have a graph of the claimed coronavirus cases in the States. The file opens with a security warning that says "Macros have been disabled". If the macro is allowed to run, it will download and run NetSupport Manager RAT.
While Netsupport Manager is a legitimate program, it is known for being abused by attackers to gain remote access, enabling them to run commands on compromised computers. NetSupport RAT used in this campaign drops multiple components that include several .dll, .ini, and other executable files. A VBScript is also installed along with an obfuscated PowerSploit-based PowerShell script. That script connects to a command and control server and allows attackers to send more commands to the hijacked computer.
This new malware campaign isn't the first we have seen that has bad actors attempting to take advantage of people during the COVID-19 pandemic. In March, security researchers discovered a home router DNS attack that spread coronavirus-themed malware. In that attack, the DNS settings of the router were changed to redirect the victim to a website that delivers the Oski infostealer malware as the final payload.