This Nasty Windows Security Exploit Gives Hackers Control Of Your PC, Patch ASAP
The vulnerability functions as a bypass for CVE-2021-1732, a vulnerability found in December of 2020 to have been actively exploited since May of that year. Microsoft patched this prior elevation of privilege vulnerability in 2021, but this new one gets around the old patch, requiring a new patch.
Microsoft accordingly released a patch for the new vulnerability as part of January 2022’s Patch Tuesday update, which included fixes for 96 other vulnerabilities as well. The vulnerability affects all versions of Windows 10 and 11, as well as Windows Server 2019 and 2022, without the patch. However, security researchers have currently found full exploits of the vulnerability only for Windows 10 and Windows Server 2019.
Patching this update is particularly critical for Windows Server admins who may have decided to skip January’s 2022 Patch Tuesday update or even rolled back to the previous version after initially installing the update on account of some significant bugs that initially accompanied it. As we reported earlier this month, the update shipped with bugs that were causing Windows domain controllers to boot loop, blocking Hyper-V initialization, disabling ReFS support, and breaking certain types of IPSEC connections. Fortunately, Microsoft has issued updates for these bugs, so Windows Server admins should install January’s update in order to receive the patch for this latest elevation of privilege vulnerability.
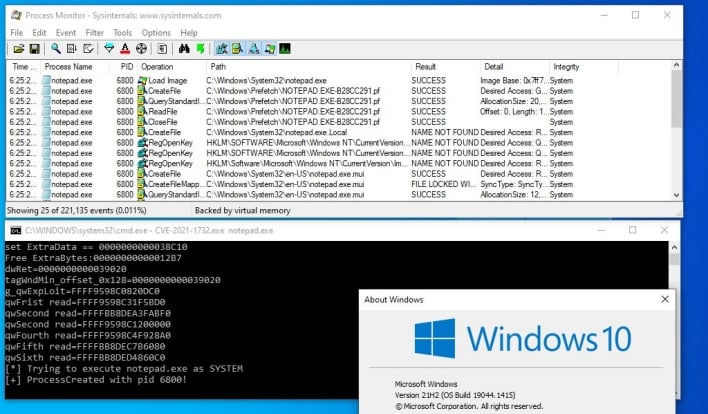
You can read more about the vulnerability on Microsoft’s public notice of disclosure or RyeLy’s breakdown.

