Sinister MacStealer Malware Steals Mac Passwords And Other Private Data
Uptycs researchers recently uncovered a new malware that targets macOS desktop and laptops and shared details on their blog. It's called MacStealer and can infect machines with Intel, M1 and M2 CPUs, plus macOS Catalina and above. The researchers found that the threat actor distributing MacStealer can snag passwords, files, credit card info, images, iCloud Keychain info, etc. Whatever information it collects is then sent via the threat actor's Telegram bot account.
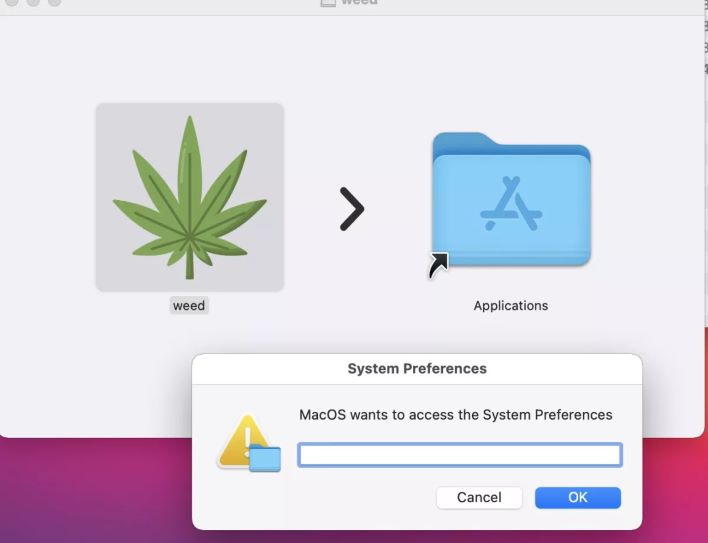
The research team discovered the malware on online hacking forums, although they haven't disclosed how the malware is and ultimately will be distributed. MacStealer is poses as a DMG (macOS installer file) called "weed.dmg". Unlike a broader interest item, it seems like this malware eyes a specific target audience, for the time being anyway.
Regardless, once a victim launches the file, the script requests the user's password, which as you can already guess, is the start of a lot of troubles. The malware will begin accessing files and data from the infected machine, plus passwords, cookies, and credit card info through Google Chrome, Brave, and Firefox browsers. A new version of the MacStealer will be able to collect data from Safari and Apple Notes.
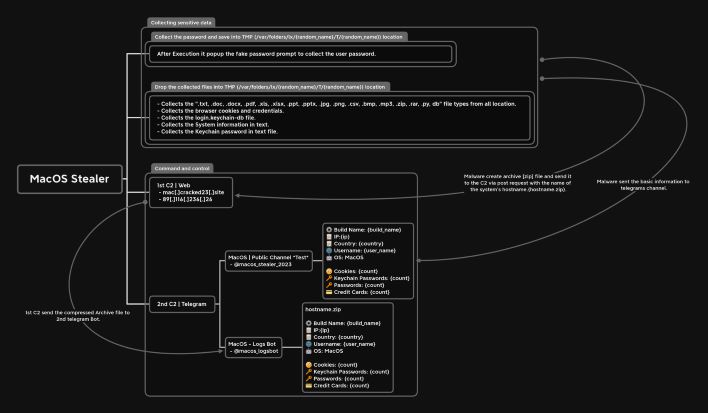
MacOS-targeting malware is more prevalent than many realize, so it's definitely wise for Mac users to keep their defenses up. There is currently no quick way to solve or fix this malware, so the best things to do are to stay away from suspicious install files, as well as ensure that your macOS device(s) have the latest software updates. In fact, Uptycs found that the distributor of MacStealer has a large production order from other threat actors, which means you can expect to see MacStealer more frequently.

