SEO Poisoning Campaign Laces Your Zoom And TeamViewer Installs With BATLOADER Malware
The Mandiant team found that this campaign has two different infection chains. The first infection chain targets users looking for software bundles. A user who searches for something like “free software development tools installation” may see a compromised website among the search results on the first page and visit that site. If the user downloads and runs the software installer on the compromised site, it will install legitimate software, but bundled with that software is BATLOADER malware.
Once the BATLOADER malware is executed as part of the installation process, a multi-stage infection chain begins, where each stage involves downloading and executing an additional malicious payload. One of these payloads contains malicious VBScript embedded inside a legitimate internal component of Windows, AppResolver.dll. Despite the malicious VBScript, the DLL sample’s code signature remains valid, which is an issue that Microsoft attempted to address with a patch for CVE-2020-1599.
In a later stage of this attack chain, the malicious payload installs additional malware, as well as ATERA. However, the second attack chain skips over the previous steps and installs ATERA directly.
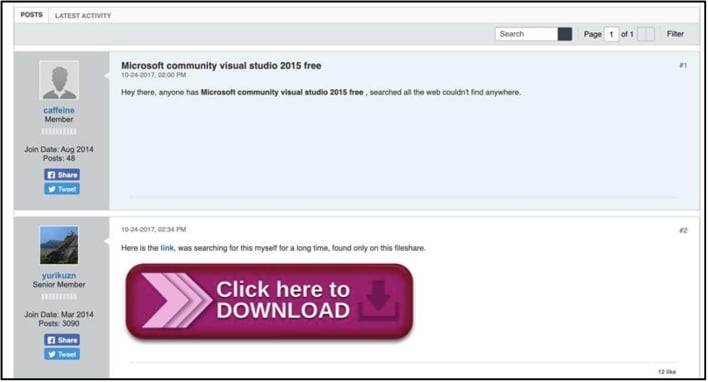
Users directed to the malicious website will find a message board with a download link for what appears to be legitimate software, but is really the ATERA Agent Installer Package. ATERA is legitimate Remote Monitoring and Management (RMM) software, but the threat actors in this case use it to run pre-configured scripts, perform malicious tasks, install persistent malware, and finally uninstall itself, once its work is done.
According to Mandiant, some of the attack chain activity overlaps with techniques used in CONTI ransomware operations. The threat group behind this SEO poisoning campaign may be replicating CONTI techniques, by drawing on training documents, playbooks, and tools that were leaked by a disgruntled CONTI affiliate in August 2021.
Mandiant’s report on the SEO poisoning campaign contains further details, including some of the malicious domains being used in the campaign, as well as MD5 hash values of malicious packages used in the campaign.

