Security Researcher Finds 34 Windows Driver Flaws That Allow Full Takeover
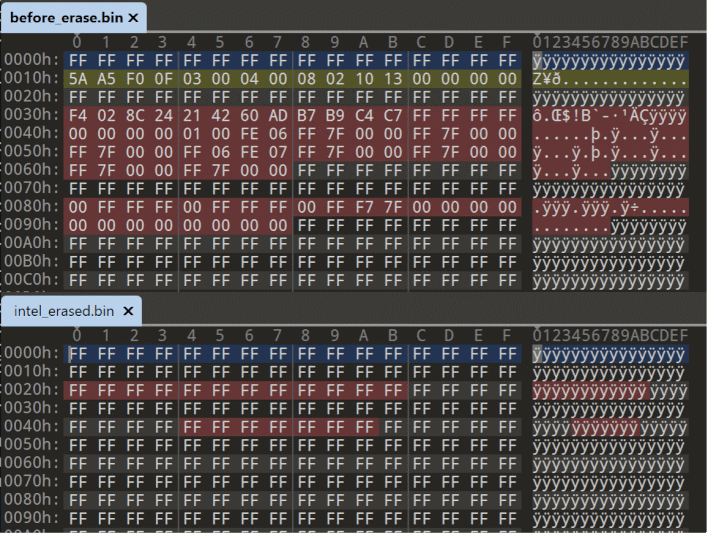
Those aren't the only functions that some of these drivers allow. Six of the drivers grant kernel-level memory access, allowing an attacker to elevate themselves or really do whatever they want. An additional twelve of the drivers could allow a bad actor to modify the system's model-specific registers (MSRs.) This could allow them to bypass and disable security features and exploit mitigations, or simply crash the system.
Many of the exploitable drivers that TAU found are from major vendors, like Intel, AMD, and Dell, just to name a few. These aren't shady third-party programs downloaded from some sketchy malware site, but official drivers installed by these corporations for their own purposes—typically firmware updates.Affected drivers: stdcdrv64.sys, IoAccess.sys, GEDevDrv.SYS, GtcKmdfBs.sys, PDFWKRNL.sys, TdkLib64.sys, phymem_ext64.sys, rtif.sys, cg6kwin2k.sys, RadHwMgr.sys, FPCIE2COM.sys, ecsiodriverx64.sys, sysconp.sys, ngiodriver.sys, avalueio.sys, tdeio64.sys, WiRwaDrv.sys, CP2X72C.SYS, SMARTEIO64.SYS, AODDriver.sys, dellbios.sys, stdcdrvws64.sys, sepdrv3_1.sys, kerneld.amd64, hwdetectng.sys, VdBSv64.sys, nvoclock.sys, rtport.sys, ComputerZ.sys, SBIOSIO64.sys, SysInfoDetectorX64.sys, nvaudio.sys, FH-EtherCAT_DIO.sys, atlAccess.sys
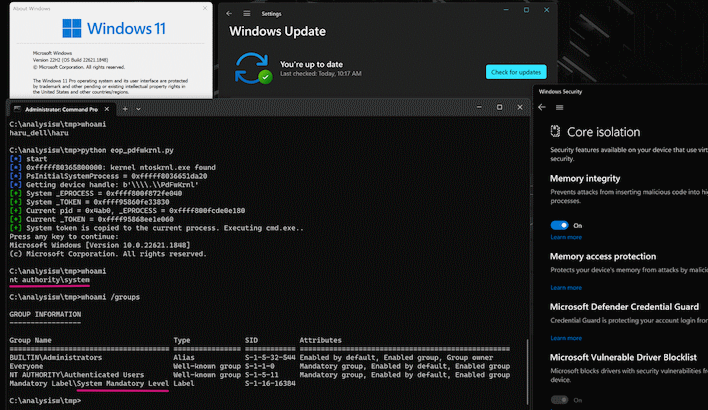
Concerningly, while TAU reported these flaws to the vendors, only two of them actually fixed the problems. Phoenix Technologies patched its TdkLib64.sys driver, and AMD updated PDFWKRNL.SYS, too. That leaves numerous exploitable drivers out there in the wild, although up-to-date version of Windows 11 will block a few of them through its Hypervisor-Protected Code Integrity feature. HVCI is supposed to work on Windows 10, too, but security researcher Will Dormann remarks that it seems to be ignoring the driver blocklist at this time.


