Over 100 Million IoT Devices Vulnerable To New NAME:WRECK Remote Execution Attacks
Forescout reports that the NAME:WRECK vulnerabilities are bugs within TCP/IP stacks FreeBSD, Nucleus NET, IPnet, and NetX. These stacks are used in millions of different devices, and when paired with the “often external exposure of vulnerable DNS clients,” the attack surface can be quite a large target. The researchers specifically claim that organizations in healthcare and government sectors are “in the top three most affected for all three stacks,” meaning they could be most vulnerable and easily targeted.
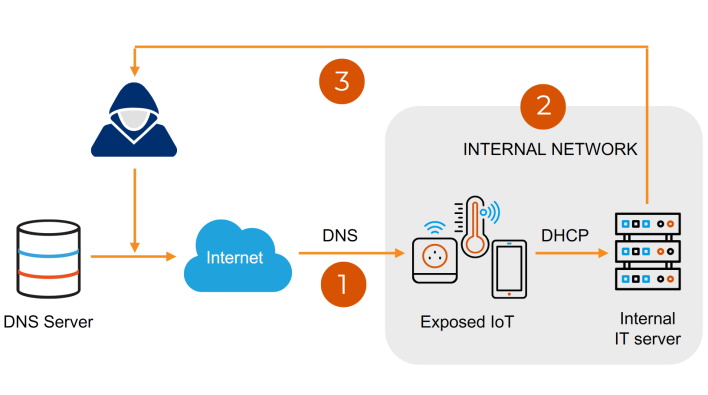
To avoid this very possible security breach situation, organizations need to patch devices running the vulnerable versions of the TCP/IP stacks. As Forescout states, FreeBSD, Nucleus NET, and NetX have been patched recently, so “device vendors using this software should provide their own updates to customers.” However, if this is not possible, organizations need to enforce network segmentation and proper network hygiene to mitigate risk. Either way, hopefully, NAME:WRECK will put more eyes on vulnerable network stacks, and consumers can face fewer cybersecurity threats in the future.


