More details continue to emerge regarding the
hacking incident involving NVIDIA and a group taking credit for the security breach, Lapsus (or "LAPSU$" as the entity prefers to stylize it). Days after the breach hit headlines, NVIDIA has confirmed the incident, noting that some proprietary information was indeed stolen. At the same time, it is downplaying reports of ransomware being involved.
The general idea behind ransomware is to encrypt a victim's data and threaten to permanently delete it unless a ransom is paid, often in Bitcoin due to the relative anonymity that cryptocurrency provides. Ransomware can also be more loosely applied to stealing and then threatening to make public sensitive details unless certain demands are met. Either way, it amounts to extortion.
In this case, it was reported that
Lapsus stole 1TB of data from NVIDIA, including schematics, driver source code, firmware details, and more. The group also claimed it was in possession of a tool to completely bypass NVIDIA's low hash rate limiter on its GeForce series graphics cards, and said it would "forget about the hw folder (it's a big folder)" if NVIDIA pushed a firmware update to remove the LHR lock on affected GPUs.
As the story developed, it was reported that
NVIDIA returned the favor and hacked back at Lapsus, or so the group claimed. The group accused NVIDIA of returning fire with ransomware of its own, but "luckily we had a backup."
So what the hell is actually going on? That's still not clear, though NVIDIA said in a statement to HardwareLuxx that it was a victim of a data breach.
"We are investigating an incident. Our business and commercial activities continue uninterrupted. We are still working to evaluate the nature and scope of the event and don’t have any additional information to share at this time," NVIDIA initially said.
NVIDIA provided a follow-up statement with more details, noting that hackers made off with employee credentials and proprietary information. Here's the
statement in full...
"On February 23, 2022, NVIDIA became aware of a cybersecurity incident which impacted IT resources. Shortly after discovering the incident, we further hardened our network, engaged cybersecurity incident response experts, and notified law enforcement.
We have no evidence of ransomware being deployed on the NVIDIA environment or that this is related to the Russia-Ukraine conflict. However, we are aware that the threat actor took employee credentials and some NVIDIA proprietary information from our systems and has begun leaking it online. Our team is working to analyze that information. We do not anticipate any disruption to our business or our ability to serve our customers as a result of the incident.
Security is a continuous process that we take very seriously at NVIDIA – and we invest in the protection and quality of our code and products daily.
Proprietary information could be just about anything, from the inner workings of NVIDIA's GPU architectures to, as the group previously claimed, firmware and driver details, and everything in between.
Information continues to trickle out. For example, some of the leaked data contains reference to future GPU architectures, including Blackwell, which is though to succeed Hopper. In addition, an anonymous source apparently sent what they claim is proof of stolen DLSS source code to the folks at TechPowerUp.
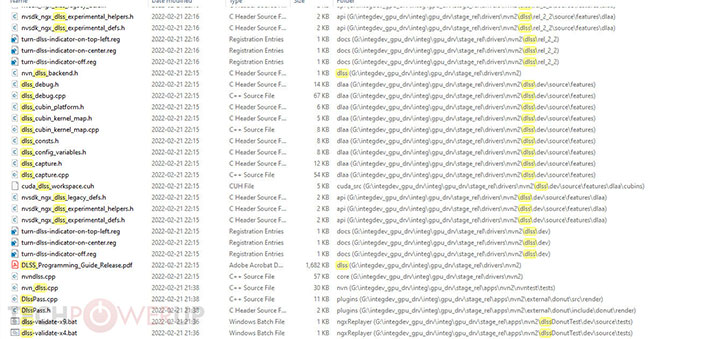
It amounts to a screenshot of a folder containing a whole bunch of DLSS-related files. The screenshot itself doesn't divulge any sensitive information, but if proves to be legitimate, it means the hackers are likely in possession of DLSS source code.
You can see in the screenshot above there's a programming guide, C++ source files, Windows batch files, and more. The data dump also suggests the stolen source code pertains to a recent version of DLSS (version 2.2), as opposed to the original release.
If these details are made public, it could open up a world of consequences, both legal and as it pertains to what open source developers could do with the information. It will be interesting to see how this ultimately plays out.