MyDeal's Data Breach Exposing 2.2M Customers Just Went From Bad To Worse
Neither MyDeal nor Woolworths Group has offered an explanation for how the threat actor came into possession of the credentials that enabled the data breach. Furthermore, neither company makes clear whether the threat actor directly accessed the CRM system or first gained unauthorized access to MyDeal’s wider internal network. The threat actor shared a map of MyDeal’s network infrastructure, as well as screenshots that appear to show unauthorized access to the company’s Amazon Web Services (AWS) portal, Confluence workspace platform, and Zendesk customer support system. The threat actor also claimed to have stolen source code from MyDeal’s Bitbucket repositories.
This information would seem to indicate that the threat actor accessed not just MyDeal’s CRM system, but also its wider network. Fortunately, while Woolworths Group completed its acquisition of MyDeal just last month, the two company’s networks operate on separate platforms, so the breach remained isolated to MyDeal’s network.
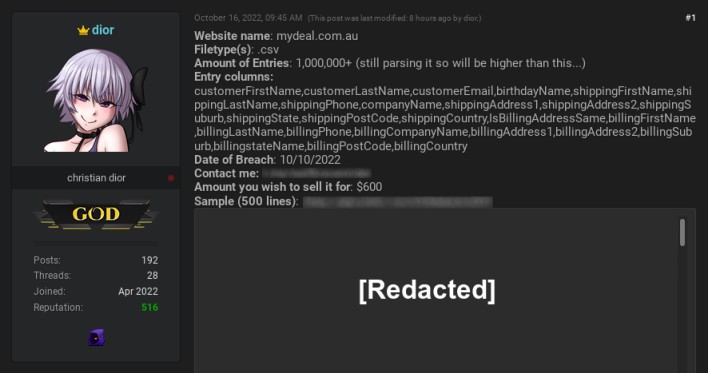
The seller has also indicated that there won’t be any more copies of the data sold. It’s possible that MyDeal or Woolworths Group hired an intermediary to buy back the stolen information without the seller’s knowledge, as T-Mobile once did. However, unless Woolworths Group or its subsidiary issues a statement claiming to have done so, MyDeal customers affected by the breach should assume that their information was sold to another cybercriminal and may be used to commit identity fraud or conduct phishing attacks.
According to Woolworths Group, 1.2 million of the 2.2 million affected customers had just their email addresses exposed in the data breach. The stolen information belonging to the remaining customers includes first and last names, email addresses, phone numbers, shipping and billing addresses, and dates of birth. MyDeal has notified all affected customers by email and stated that anyone who has not received such a notice by email was not affected.

