Microsoft Sounds Urgent Warning On An Active Windows Update Security Flaw
Actually, sorry; make that four zero-days. If you're not up on your security jargon, a 'zero-day' is a security exploit that is already being actively abused when it is discovered. Indeed, Microsoft sewed up zero-day flaws in Office Publisher, Windows Mark of the Web, the Windows Installer, and Windows Update in this month's update rollup.
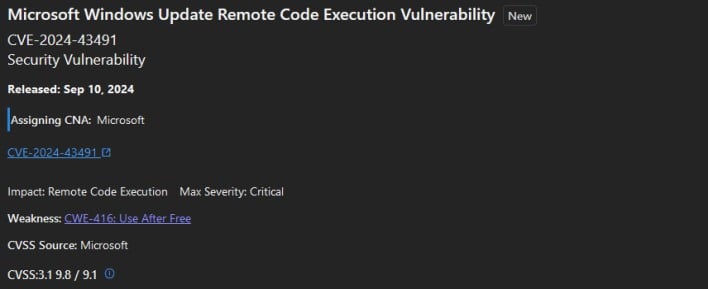
The flaw seems to have actually been caused by Microsoft itself, as the vulnerabilities that offered the attack surface were actually already patched once, but a security update released in March broke the mitigations for those vulnerabilities. As we noted, the flaw only affects Windows 10, but the other, less-severe zero-days are more general and include Windows 11.
Ultimately, what you need to know is that Microsoft has these problems all patched up. Simply download the latest security updates—your machine probably did this for you already—and you can sleep soundly, secure in the knowledge that a new cybersecurity nightmare will pop up next week.


