Lemon Duck Botnet Evolves To Pummel Victims Using Microsoft Exchange Server Vulnerabilities
In March, Microsoft first caught onto Lemon Duck “adopting different exploit styles and choosing to use a fileless/web shell-less option of direct PowerShell commands” for some attacks. They managed to compromise many Exchange servers, dropping cryptocurrency miners along the way, but slowly “moved in the direction of being more of a malware loader than a simple miner.”
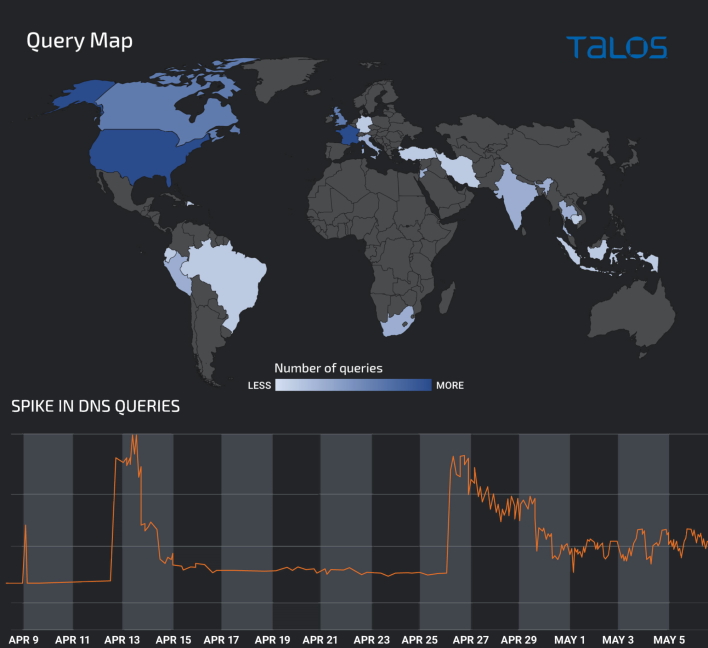
Talos’ posting noted several new Lemon Duck domains saw a spike in usage around April 9th of this year. It is reported that many of these requests “originated from North America, followed by Europe, South East Asia, with a few others from South America and Africa.” What is interesting about all of this is that Lemon Duck is changing its tactics constantly to “maximize their ability to achieve their mission objectives.” The threat actor has been found to remove antivirus products, tear down protections, and attempt to spread over networks to keep an income flow.
Whatever the attackers end up developing, companies need to be aware that hackers are always out there trying to make money and attack systems. If you happen to have an on-premises Exchange server, heed this as a warning that it needs to be patched and checked over to ensure it was not breached. Otherwise, you may have to worry about Lemon Duck soon.


