Over the weekend,
cybersecurity experts, forensics teams, and white-hat hackers worldwide have been battling the
ransomware incident affecting Kaseya VSA customers. Now, the Florida-based IT and remote management company is reporting that fewer than 60 customers and 1,500 downstream companies have been affected by this. But could this all have been prevented in the first place, or did cybersecurity take a backseat?
On the evening of July 5th, Kaseya reported that the
ransomware attack, which started on July 2nd against its VSA product, had hopefully been contained at this point. So far, there are fewer than 60 direct Kaseya customers affected; however, as many of these companies provide IT services, approximately 1,500 businesses downstream have been affected. Thankfully, there have been no new reports of compromises for VSA customers since July 3rd, nor has there been any evidence of compromise for VSA software-as-a-service customers.
Furthermore,
Kaseya has reportedly “met with the FBI/CISA tonight to discuss systems and network hardening requirements prior to service restoration for both SaaS and on-premises customers.” However, until restoration can be safely executed with Kaseya, customers should keep on-premises VSA servers offline until further instructions.
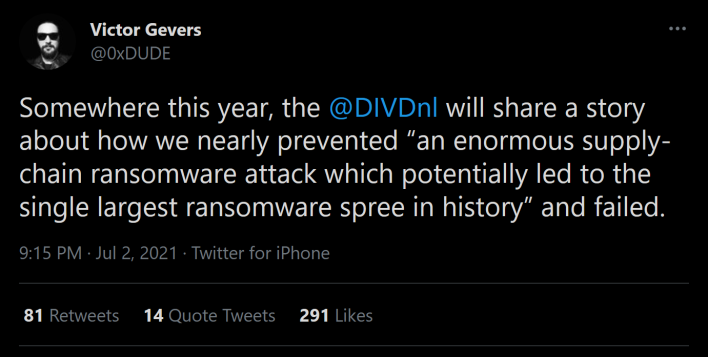
As the restoration and recovery efforts continue, it is interesting to note that this disaster was nearly avoided. Volunteer researchers at the Dutch Institute for Vulnerability Disclosure, including Wietse Boonstra, previously discovered several zero-day vulnerabilities, such as one tracked as CVE-2021-30116, which was used in the attack. Unfortunately, before DIVD and Kaseya could complete a patch and deploy it, criminal hacking group
REvil was quick to the draw on July 2nd, causing the havoc in which companies now find themselves.
Though there is a very real possibility that Kaseya put off the patch due to the holiday weekend,
DIVD reports that the company “has been very cooperative." The DIVD blog post continues, explaining that Kaseya “were willing to put in the maximum effort and initiative into this case both to get this issue fixed and their customers patched.” Ultimately, we may never really know what happened behind closed doors, but the people in cybersecurity and customer service alike trying to rectify this situation have likely worked day and night tirelessly and should be commended for the efforts.
As the chair of the DIVD alludes, hopefully, we will get to hear about how this attack was nearly prevented as we only have gotten a glimpse into the nightmare. However, there is concern that the nightmare could continue into next week as more people come online and use systems for work. Whatever ends up happening, stay tuned to
HotHardware for updates, and let us know what you make of the situation in the comments below.