How Hackers Are Using Sock Puppets To Carry Out Convincing Phishing Attacks
The most recent threat actor to make use of this technique is TA453, an Iranian threat group also known as “Charming Kitten.” Proofpoint’s research indicates that this group works to support the interests of the Islamic Revolutionary Guard Corps (IRGC). TA453 largely targets academics, policymakers, diplomats, journalists, and human rights advocates. The threat actor conducts phishing attacks by corresponding with its targets under the guise of a journalist, academic, or other individual interested in the work of the targets.
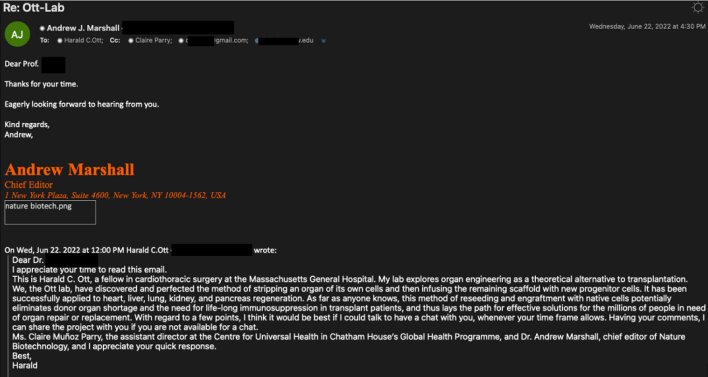
The attack began with an email sent by “Harald Ott” asking for feedback on a project related to the target’s field of research. This first email identified and cc’d two other personas by the names of “Clair Parry” and “Andrew Marshall.” “Andrew” then followed up the first email by preemptively thanking the target for his time and expressing eagerness to hear back from the target. “Harald,” “Andrew,” and “Claire” are all personas controlled by the threat actor, but their manufactured correspondence lends the appearance of legitimacy to the email chain.
The target eventually replied to the email chain, prompting “Harald” to send a further email linking to a Word document titled “Ott-Lab 371.docx. This word document downloads a macro enabled template containing three different macros. These macros collect and exfiltrate user and device information, including the user’s IP address and a list of running processes. These macros don’t appear to perform any additional malicious actions, so they may be intended for reconnaissance, with the threat actor planning to conduct further attacks later based on the software identified on victims’ machines. The malicious payload aside, this attack demonstrates that phishing attacks can come in the form of an active email chain containing multiple correspondents, making it more difficult for users to identify attacks as such before it’s too late.
Top image courtesy of Alex Brown

