Hackers Stole 130 Source Code GitHub Repos In Dropbox Data Breach
The code repositories accessed by the threat actor contained development credentials, including API keys, but Dropbox has since rotated all exposed credentials so as to prevent any further unauthorized access using the stolen keys. This mitigation step seems to have been effective, as a review of the company’s logs didn’t find any indicators that the stolen keys were successfully abused.
Besides development credentials, the affected GitHub repositories were home to Dropbox’s modified copies of third-party libraries, internal prototypes, and some of the security team’s tools and configuration files. According to Dropbox, the threat actor was not able to steal the source code for any of the company’s core apps or infrastructure, as “[a]ccess to those repositories is even more limited and strictly controlled.”
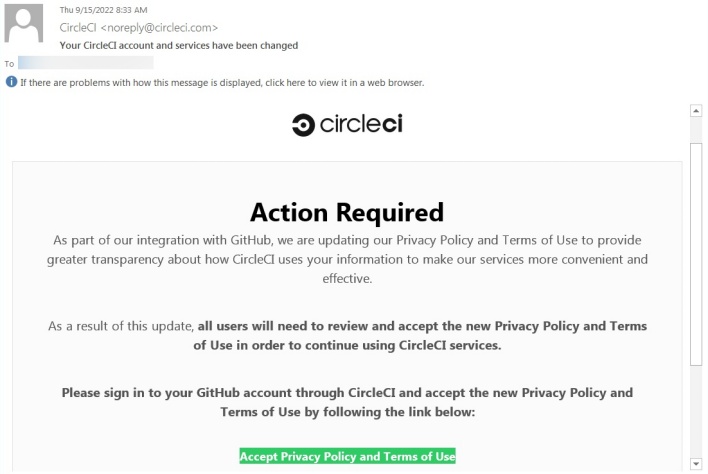
The link contained in these phishing emails sent employees to a fake CircleCI login page that asked for employees’ GitHub usernames, passwords, and one time passwords (OTP). Evidently at least one employee was duped by this phishing attempt and handed over the requested login credentials, resulting in the subsequent data breach.
Similar phishing attacks recently struck both Twilio and Cloudflare. However, the attack on Cloudflare failed because Cloudflare’s employees use hardware security keys with biometric authentication and origin binding, rather than time-based one-time passwords (TOTP), for multi-factor authentication (MFA). Origin binding locks authentication to the original login site, preventing fake phishing pages from receiving authentication codes. While Dropbox also uses hardware security keys, the company hasn’t yet completed its transition away from OTP to WebAuthn, an authentication protocol that employs origin binding. Dropbox hopes to prevent data breaches similar to this one in the future by completing its adoption of WebAuthn.

