Phishing Campaign Hooks Twilio Communications Platform, Catches Customer Data
Speaking of which, Twilio, a major communications platform that services Voice over Internet Protocol (VoIP) integrations, announced over the weekend that it was hit by a phishing attack. The threat actors behind the attack were able to gain access to some of Twilio’s internal systems and view customer data. According to Twilio, the data implicated in this breach is related to a limited number of customer accounts.
The company has partnered with an unnamed forensics firm to conduct an investigation into the incident. The investigation is still ongoing. Twilio is reaching out to affected customers to notify them of the data breach and work with them to address any problems as more details are uncovered in the investigation. Twilio customers not directly contacted and notified by the company were not affected by the breach, so far as the evidence revealed by the investigation shows.
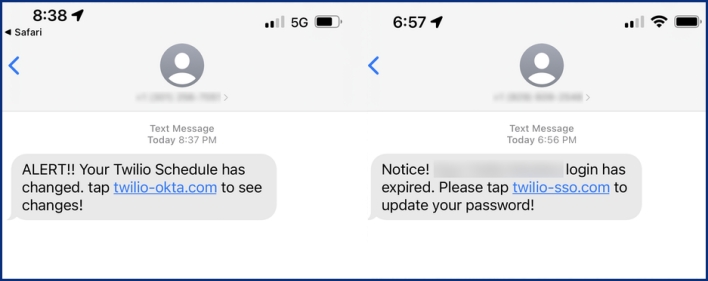
The messages falsely informed employees of expired passwords, schedule changes, or other similar notices that would require employees to login to view or address the cause for the notice. The messages prompted Twilio employees to open links to URLs that contained words such as “Twilio,” “SSO” (single sign-on), and “Okta,” which is an identity platform used by Twilio. Employees who visited these URLs were met by a webpage that mimicked Twilio’s sign-in page.
Evidently, some employees were duped by this smishing attack and entered their login credentials into the fake sign-in pages controlled by the attackers. The smishing messages were sent from phone numbers belonging to the US carrier networks, and Twilio worked with the carriers, as well as the hosting providers serving the URLs used in the attack, to shut down the malicious campaign. The Twilio Security Incident Response Team has committed to posting additional updates to the Twilio blog if there are any changes customers should be aware of.

