A security researcher who discovered a over half a dozen zero-day vulnerabilities in the Safari browser has lined his pockets with $75,000, courtesy of
Apple's bug bounty program. Left unaddressed, a few of the vulnerabilities could allow an attacker to hijack the webcam on Mac systems, as well as iPhone and iPad devices.
Ryan Pickren detailed the vulnerabilities in a pair of blog posts. He found seven in total (CVE-2020-3852, CVE-2020-3864, CVE-2020-3865, CVE-2020-3885, CVE-2020-3887, CVE-2020-9784, & CVE-2020-9787), three of which were directly related to potentially taking over the webcam or camera on
macOS and
iOS devices.
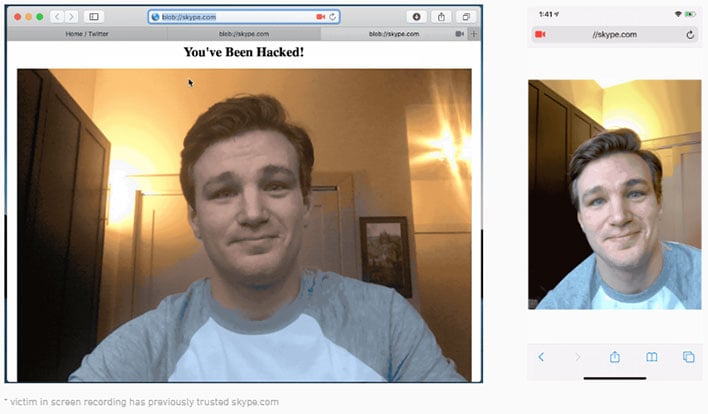
"If a malicious website strung these issues together, it could use JavaScript to directly access the victim's webcam without asking for permission. Any JavaScript code with the ability to create a popup (such as a standalone website, embedded ad banner, or browser extension) could launch this attack," Pickren explains.
 Source: Ryan Pickren
Source: Ryan Pickren
Simply put, the security flaws enabled a hacker to trick
Safari into thinking a malicious website was actually a trusted one. A hacker could then use their fraudulent identity to compromise a user's
privacy, due in part to Apple letting users permanently save their security settings on a per-website basis. As a result, a malicious website could pretend to be a trusted video conferencing portal, like Skype or
Zoom, and then gain access to the user's camera.
Pickren alerted Apple about his findings, which prompted an updated to Safari in January (version 13.0.5) that addressed three of the security flaws. Then in March, Apple rolled out another update (version 13.1) that plugged up the remaining security holes. Fortunately, there is no evidence to suggest that any of the flaws were exploited prior to being patched.
For anyone who is interested, Pickren wrote
lengthy blog post outlining the nitty-gritty technical details. As for
Apple's bug bounty program, payments range from $5,000 (minimum) all the up to $1 million.