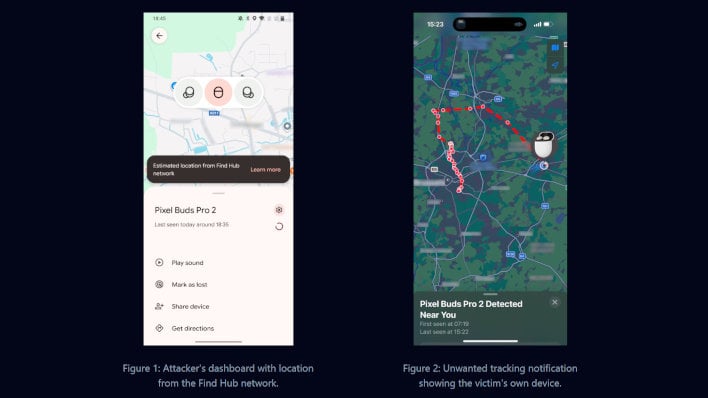
Google Fast Pair Flaw Exposes Hundreds Of Millions Of Bluetooth Devices To WhisperPair Exploit, Patch ASAP
Since the vulnerability is targeted to specific Bluetooth accessories and not smartphone OSes, both Android and iOS users are vulnerable regardless of their phone's Fast Pair settings. All that's needed is an unsecured Bluetooth device with misconfigured or outdated Google Fast Pair functionality, and typically vulnerable devices have it enabled by default. This is why updating the firmware of your Bluetooth devices is integral to fixing the issue—nothing less will do the job. The ramifications of an unsecured device are demonstrated on both the official WhisperPair web page and demonstration video uploaded to YouTube by the COSIC researchers who found the exploit.
This is a particularly concerning attack, but fortunately the fixes have already been distributed. The researchers responsible for finding it even got a healthy $10,000 bug bounty payment from Google. Unfortunately, this isn't the only major Bluetooth hardware vulnerability—ESP32 IoT devices and Airoha SoCs also suffered major vulnerabilities last year. Firmware patches are possible for these vulnerabilities, but it's difficult to surmise how many vulnerable devices actually received patches for those relatively widespread exploits. WhisperPair seems to have been dealt with relatively quickly and cleanly, however.