Dormant Colors Campaign Injects 1M Chrome Browsers With Revenue Generating Malware
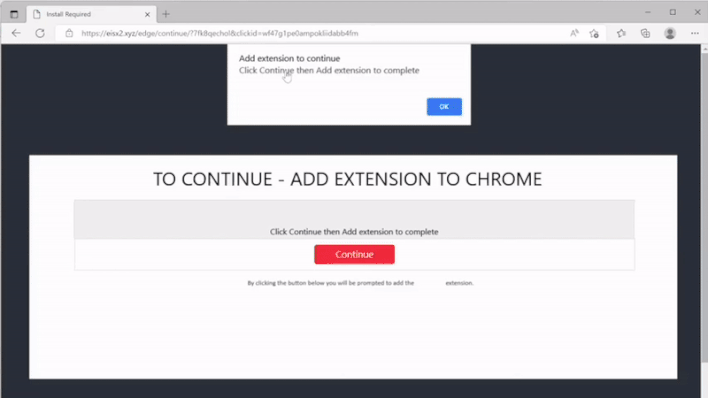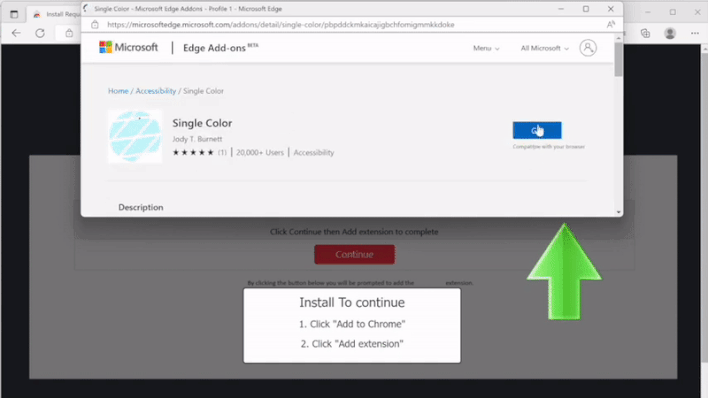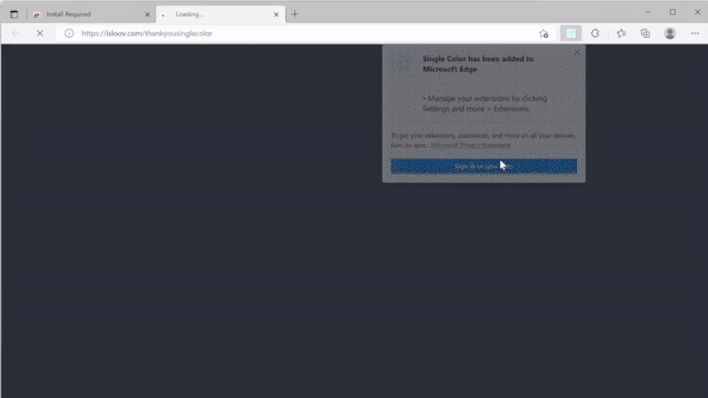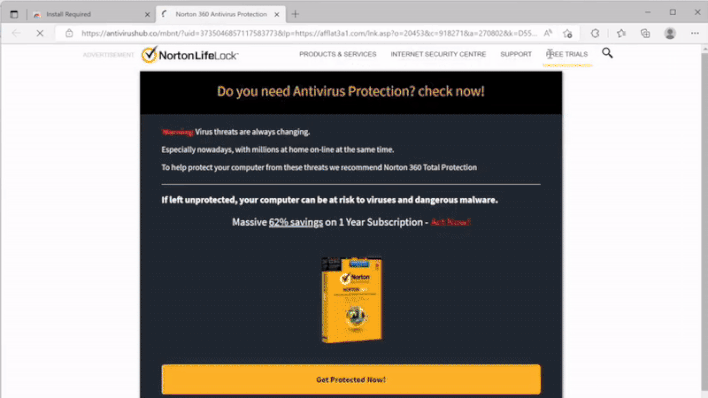
The extensions are promoted by way of malvertisments (malicious advertisements) shown on webpages redirecting users to free streams or downloads of digital media content. As shown in the GIF above, these malvertisements render fake pop-ups informing users that they can’t continue to the next page without installing an extension. If a user accepts the prompt, the Chrome Web Store or Edge Add-ons store will open in a new window, while the malvertisement in the original window instructs the user to install the browser extension shown in the new window.
Once the extension is installed, it will open a blank page, then redirect the user to a webpage showing an ad for some other service or browser extension. However, unbeknownst to the user, the blank page that briefly appears before the advertisement contains a PHP resource full of malicious scripts that the browser extension downloads and side-loads. The extensions featured in this malware campaign are promoted as tools to change the background color of websites, prompting the researchers to name the campaign “Dormant Colors” in reference to the fact that the color extensions’ lie dormant until the malicious scripts are side-loaded.
Upon loading the malicious-scripts, the extensions establish connections with the threat actor’s command and control (C2) server, which can push out additional malicious scripts to update the extensions’ behavior. The malicious extensions inject code into every webpage users visit, enabling the extensions to collect information about victims’ browser behavior, which the extensions upload to the C2 server. The researchers fear that these extensions could be used to conduct targeted phishing (spear phishing) attacks based on the information collected and shared with the threat actor behind this campaign.
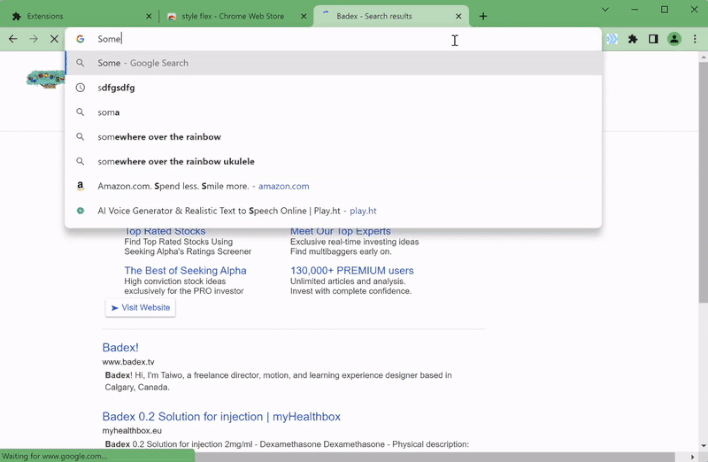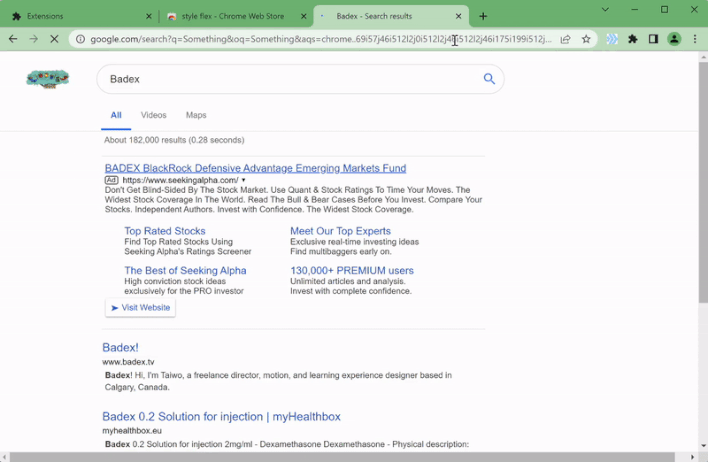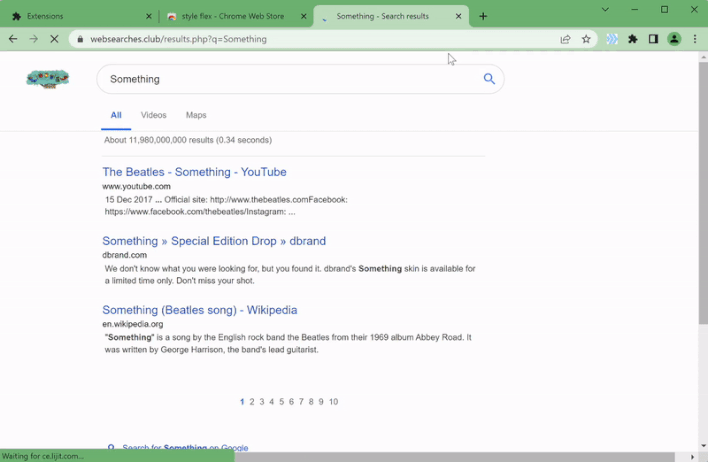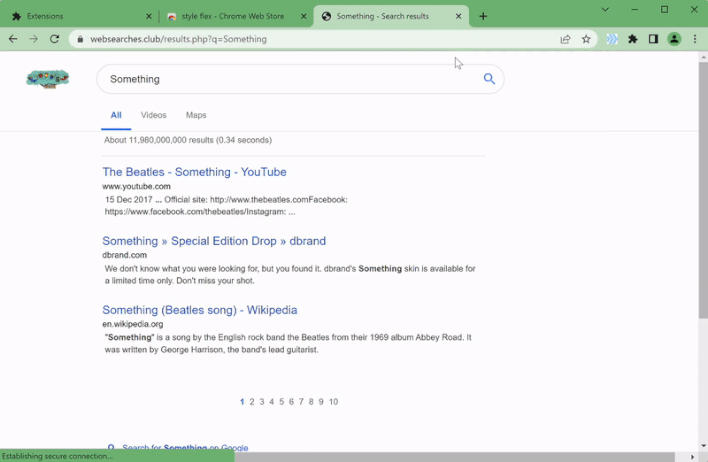
However, the researchers don’t currently have any evidence that such attacks are taking place. Instead, the extensions detect when users visit particular domain names and redirect users to either the same domain name with an affiliate code added to the URL or an alternate domain name hosting a website that appears similar to the one hosted on the domain name entered by the user. For example, the GIF above shows one of the malicious extensions redirecting the user’s Google search query to an alternate search provider that appears almost identical to Google search.
So far, the redirections performed by these malicious extensions seem to be intended to generate revenue for the threat actor behind this campaign. However, as already mentioned, these extensions could be leveraged to redirect unsuspecting victims to phishing login pages in order to steal their user credentials. Fortunately, the malicious extensions identified by Guardio appear to have been removed from both the Chrome Web Store and Edge Add-ons store, but users should make sure they don’t have any of the following extensions already installed in their browsers:
- Action Colors
- Power Colors
- Nino Colors
- More Styles
- Super Colors
- Mix Colors
- Mega Colors
- Get colors
- what color
- Single Color
- colors scale
- style flex
- Background Colors
- more styles
- Change Color
- Dood Colors
- refrech color
- imginfo
- WebPage Colors
- hex colors
- soft view
- border colors
- colors mode
- Xer Colors

