DeepSeek AI Stumbles As Sensitive User Data Is Exposed To The Web
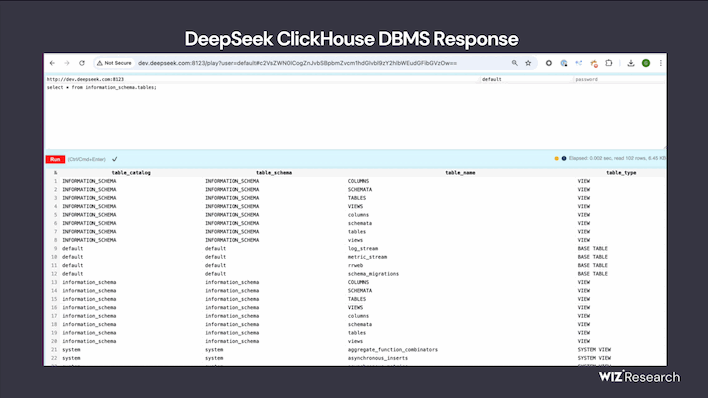
The folks who found it claim that "a publicly accessible database belonging to DeepSeek allowed full control over database operations, including the ability to access internal data." Oh boy.
While this database was hidden from a casual investigation—i.e. it wasn't linked anywhere on DeepSeek's pages—it was sitting wide open with no authentication required on port 9000 at two of the company's domain servers. Wiz says that the database included "a significant volume of chat history, backend data, and sensitive information, including log streams, API secrets, and operational details."
A Reuters report quoted Wiz's co-founder Ami Luttwak, noting that "they took it down in less than an hour, but this was so simple to find, we believe we're not the only ones who found it." That could be very concerning for anyone who has used the DeepSeek app on their Android or iOS devices.
We won't repeat all of Wiz's findings here; if you want to read all about the breach, you can hit the company's blog post for more information. However, this display of gross incompetence does throw some shade on DeepSeek's accomplishments. Perhaps the company full of AI engineers doesn't employ a cybersecurity expert? They probably should get on that.