Chinese State-Sponsored Hackers Stole US Intellectual Property Unnoticed Since 2019
Researchers at Cybereason recently informed the US Federal Bureau of Investigation (FBI) and Department of Justice (DOJ) about a malicious campaign to steal intellectual property from North American, European, and East Asian technology and manufacturing companies. According to Cybereason, this ongoing intellectual property theft operation can be attributed to a Chinese state-sponsored hacking group dubbed “Winnti.” The group is also known as advanced persistent threat (APT) 41, BARIUM, and Blackfly. The researchers named this cyber espionage campaign “Operation CuckooBees.”
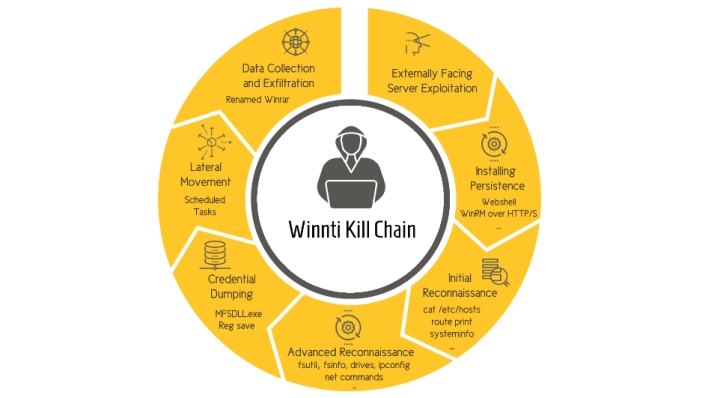
Operation CuckoBees took the form of a sophisticated multi-stage attack that hid from traditional antivirus software by abusing Windows Common Log File System (CLFS) and manipulating NTFS transactions (NFTS being Microsoft’s file system). CFLS log files can’t be viewed by antivirus software or users, meaning the attackers could gain a foothold in a virtually unnoticeable manner. The hackers also avoided detection of suspicious activity during reconnaissance by using common Windows commands like “ipconfig,” “systeminfo,” and “ping.” Once the hackers identified valuable data, they were able to exfiltrate it with a portable command-line WinRAR app signed with a valid digital signature.
Cybereason has published multiple reports detailing the tactics, techniques, malware, and exploits used by Winnti in Operation CuckoBees.

