Ransomware Gang Leaks 43GB Of Boeing Data After Demand To Pay Up Doesn't Fly
Toward the end of October, the Lockbit group posted that they had compromised Boeing and made off with a significant amount of sensitive data. The deadline to complete negotiations was November 2nd before the group would leak said data. At first, it seemed that Boeing was engaging with the threat actors after the listing was pulled down. However, Boeing was relisted on November 7th, and six days later, the data was published.
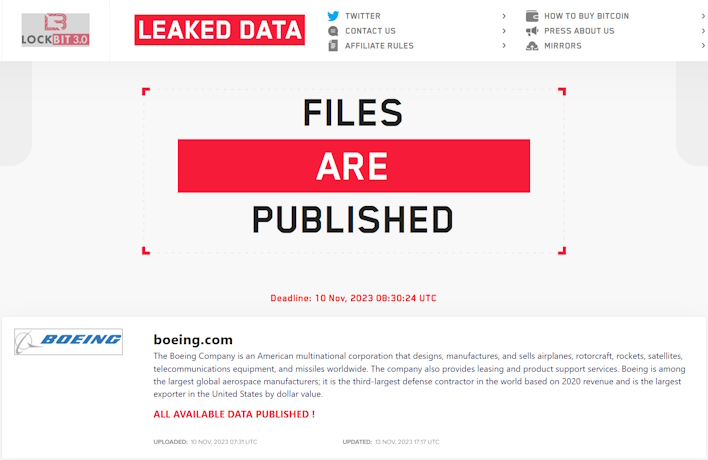
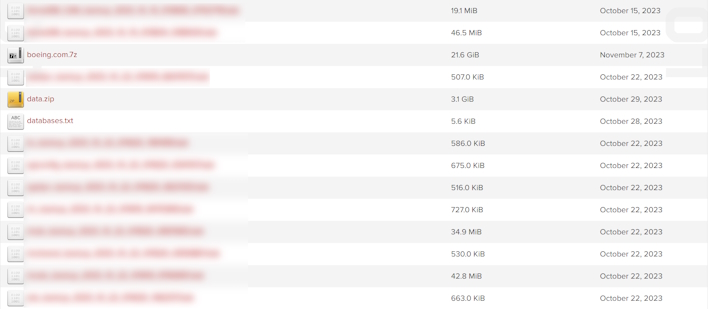
The data, which is now available through Lockbit’s website, includes what appears to be primarily backup files from a handful of different systems, such as Citrix Xen Desktop, Ivanti Service Management, and others. We have not gone through what is available, but this sort of information provides threat actors invaluable insights into the inner workings of Boeing’s network. With that, other threat actors might have an easier time getting into Boeing, especially if any new relevant vulnerabilities crop up in the future.
At the end of the day, this is only one breach in a long list of breaches, especially from LockBit, as these sorts of threat actors work to outpace efforts to prevent the attacks. In this case, though, we hope the Boeing breach will serve as a good reminder to the company and others to stay on top of cybersecurity, to prevent future attacks due to leaked internal infrastructure knowledge. We will have to see, so stay tuned to HotHardware for coverage of Boeing’s breach and other cybersecurity events.