LockBit Ransomware Gang Takes $70M Chip Shot At TSMC After Alarming Security Breach
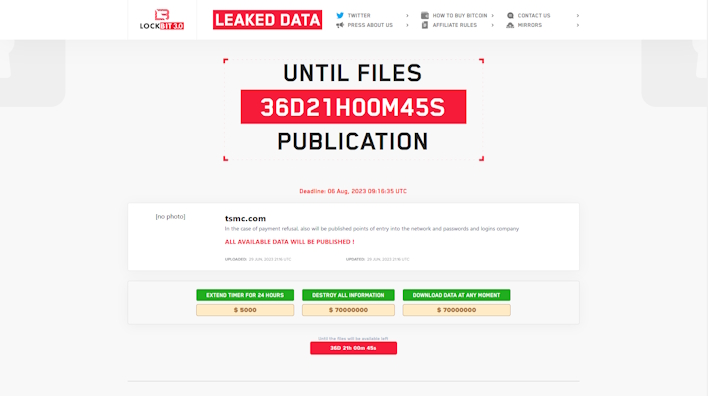
Overnight, threat actors affiliated with LockBit posted a $70 million ransom for TSMC’s data to be deleted or downloaded. According to reports from researchers at vxunderground, this attack comes from the National Hazard Agency, a “sub-clique of Lockbit ransomware group.” The below screenshot from vxunderground shows what is believed to be the threat actors in a TSMC HP Enterprise storage server to prove they are in TSMC’s systems.
When asked for comment, TSMC says that this is a third-party breach “which led to the leak of information pertinent to server initial setup and configuration.” TSMC continues, saying the following:
Upon review, this incident has not affected TSMC’s business operations, nor did it compromise any TSMC’s customer information. After the incident, TSMC has immediately terminated its data exchange with this supplier in accordance with the company’s security protocols and standard operating procedures. TSMC remains committed to enhancing the security awareness among its suppliers and making sure they comply with security standards. This cybersecurity incident is currently under investigation that involves a law enforcement agency.
The supplier that was breached is Kinmax Technology Inc., a systems integrator who provided a statement through TSMC that reported the company “discovered that our internal specific testing environment was attacked, and some information was leaked.” The data in this breach “mainly consisted of system installation preparation that the Company provided to our customers as default configurations.”
Given this information, we have reached out to LockBit and National Hazard Agency for comment and are awaiting a response. Until then, here is what we know. TSMC, at the time of writing, has until August 6th to pay the $70 million ransom before the supposed data LockBit has is leaked. However, it is unclear what that data is exactly, especially given TSMC claims that this is a third-party breach that does not affect them as “every hardware component undergoes a series of extensive checks and adjustments, including security configurations, before being installed into TSMC’s system.”
The threat actors, however, may have managed to gain access to at least one of TSMC’s systems given the screenshots above and unconfirmed sources we are seeing. Subsequently, this is an evolving situation, so stay tuned to HotHardware for updates.
Update, 6/30/2023 - 10:53 AM EST
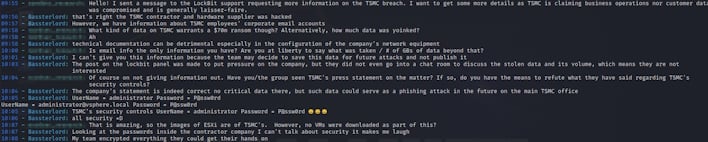
A supposed member of National Hazard Agency (NHA), "Bassterlord," responded to our messages. They explained that not only did the group acquire information on the corporate email structure of TSMC, but also gained access to TSMC's VMWare environment though the third-party contractor Kinmax. You can read a portion of the conversation for yourself in the screenshot below, which was followed by a listing of the internal IPs theoretically linking to ESXi boxes and purported username and password for each indicating rampant password reuse.